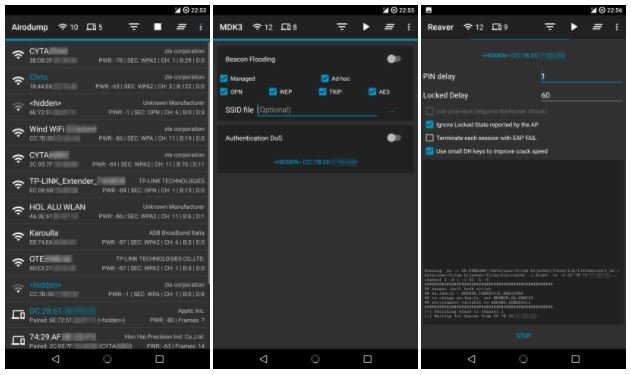
Hack any wireless network using all in one tool: Hijacker
To begin with, the experts explain that Hijacker is a graphical user interface for the penetration test tools Aircrack-ng, Airodump-ng, MDK3 and Reaver. This application offers a simple and easyRead More →