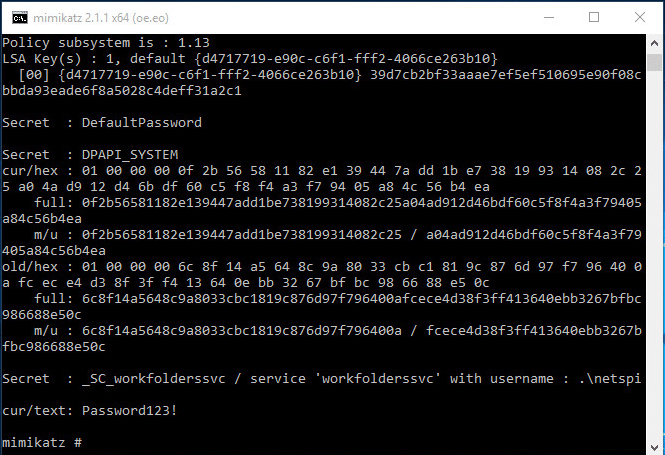
Raw sockets backdoor gives attackers complete control of some Linux servers
“Chaos” gives attackers, and follow-on attackers, full control over infected boxes. A stealthy backdoor undetected by antimalware providers is giving unknown attackers complete control over at least 100 Linux servers thatRead More →