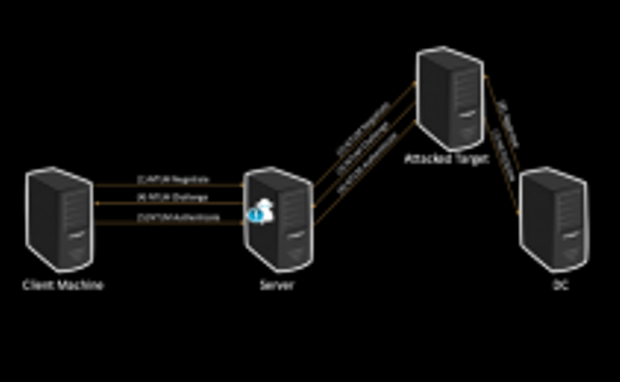
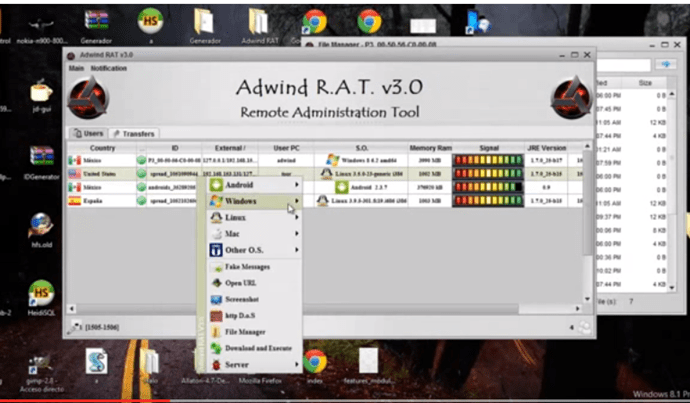
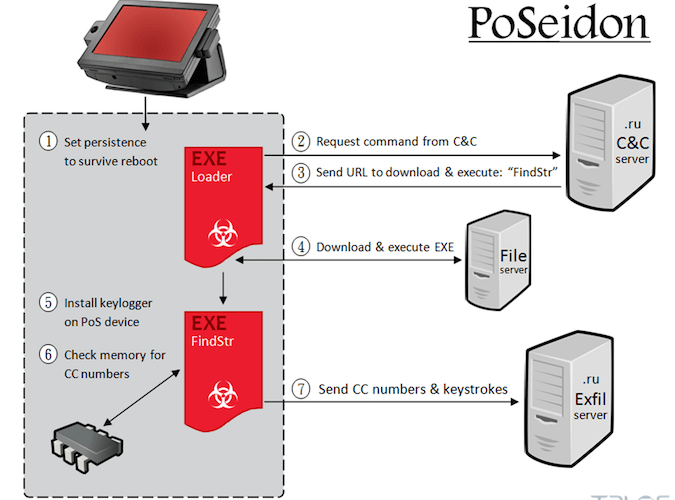
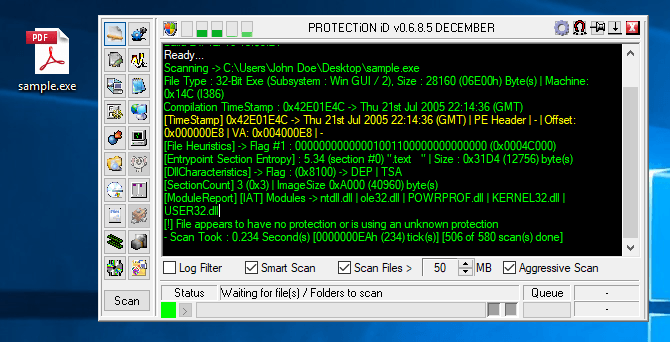
TELEGRAM-CONTROLLED HACKING TOOL TARGETS SQL INJECTION AT SCALE
A black market hacking tool has the potential to rapidly conduct website scans for SQL injection vulnerabilities at a large scale, all managed from a smartphone through the Telegram messenger.Read More →