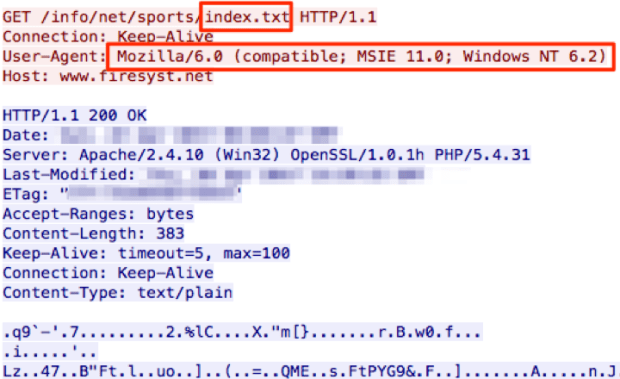
Thieves drain 2fa-protected bank accounts by abusing SS7 routing protocol
The same weakness could be used to eavesdrop on calls and track users’ locations. A known security hole in the networking protocol used by cellphone providers around the world playedRead More →