HTTPoxy Vulnerability Affects CGI-Based Apps in PHP, Python, and Go
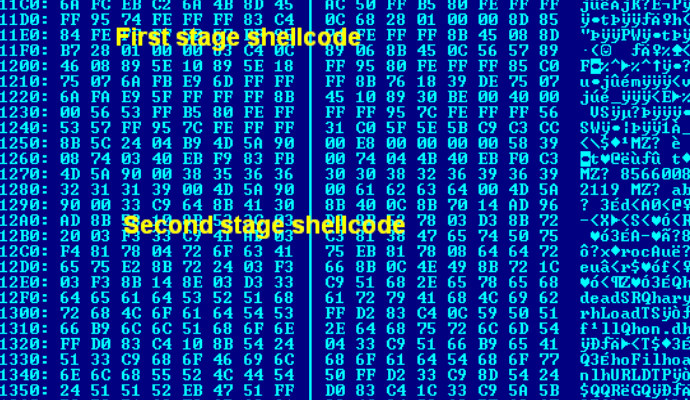
Fifteen-year-old vulnerability comes back to life. HTTPoxy is the name of a 15-year-old vulnerability that has plagued several code libraries that make HTTP requests, and has most recently been found toRead More →