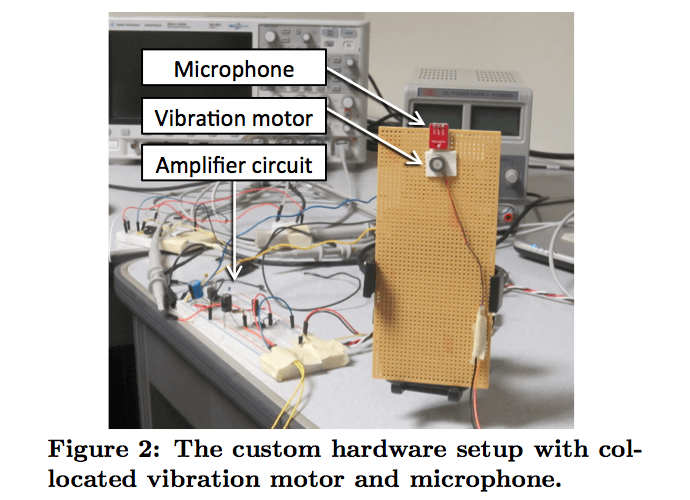
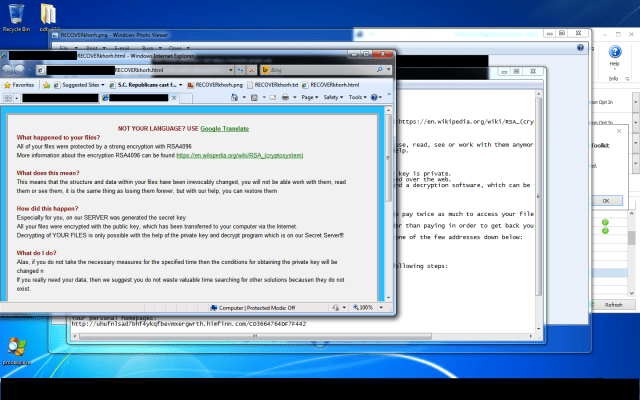
Researchers Turn Smartphone Vibration Motor into Microphone to Spy on You
VibraPhone attack turns smartphones into listening devices. Two researchers from the University of Illinois at Urbana-Champaign have devised a method for turning vibration motors, like the ones found in smartphones, intoRead More →