As many iPhone users may have noticed, the iOS 14.5 update includes an unlock feature using the Apple Watch. The feature was included in order to unlock the smartphone with facial recognition even if the user is wearing a mask, although many already wonder if this feature does not pose a security risk.
Recently a researcher detailed how his daughter was able to easily unlock her smartphone, first mentioning that she previously used a Samsung Galaxy Android device, although she tried to find on the iPhone 12 Pro Max a device with better security features.
The latest version of the system allows you to unlock your device even if the user is wearing a mask, which requires linking an Apple Watch to the iPhone and keeping it in a location near the device. The problem is that your device allows too wide a distance between your Apple Watch and your iPhone.
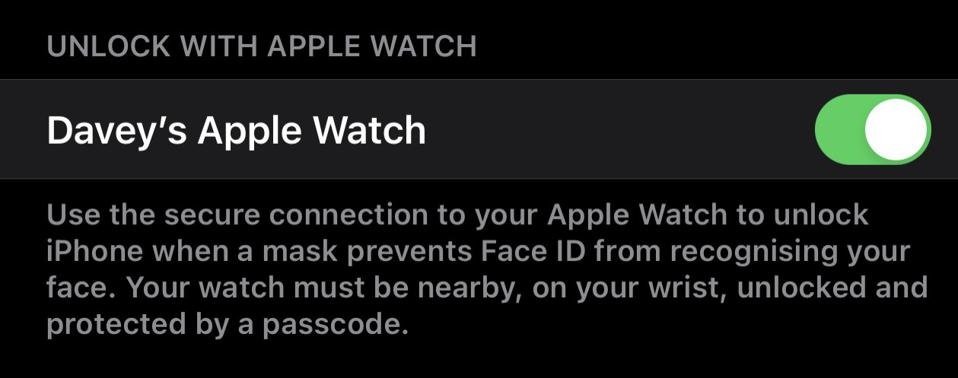
Jack Moore, ESET cybersecurity specialist, mentions how he got acquainted with this new device: “After setting up iOS 14.5, I asked my eight-year-old daughter to test system security. She put on a mask and immediately accessed the phone while standing next to it; I was notified on my watch that the phone was unlocked and I had the option to block it, although this could be circumvented relatively easily by threat actors,” Moore says.
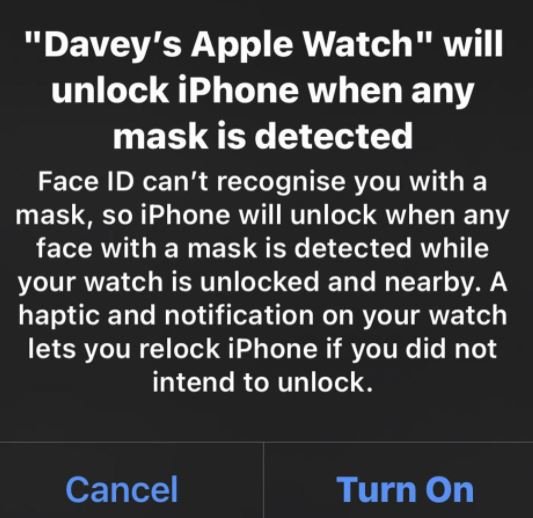
The researcher continued to conduct tests with the help of his partner, who also used a mask: “We went to opposite ends of the house and the iPhone unlocked in the same way, regardless of whether my partner looks nothing like me, even with the face shield on.” Moore mentions that this new feature is not based on Face ID to recognize the user trying to unlock the device: “Even when this feature is enabled the device mentions that it will unlock when any face with mask is detected if the iPhone detects that the linked Apple Watch is nearby,” adds the expert.

One thing worth noting is that if you use the iPhone lock button on your Apple Watch, the unlock feature is disabled until the user enters their password. This would prevent someone from having immediate access to the device, although the security hole created by this new feature should not be ignored.
Moore believes that using this feature is not recommended, at least until Apple implements a more appropriate security mechanism: “This may not be such a bad idea, although its implementation for now is too permissive and it would be worth it for Apple to make some modifications.”
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











