A report presented by Kaspersky Labs experts points to the detection of a Chinese cyberespionage group that has attacked multiple targets in South Asia since mid-2020. Identified as GhostEmperor, this group has access to sophisticated hacking tools and seems to focus on generating persistence on affected systems by using a functional rootkit even on protected and updated systems.
Kaspersky believes that hackers find their entry point to affected systems on public servers, using exploits for Apache, Microsoft Exchange and Oracle servers for the initial compromise and subsequently switching to critical systems on the affected network. Experts also mention that hackers use a wide variety of scripts for injecting a backdoor into compromised networks.
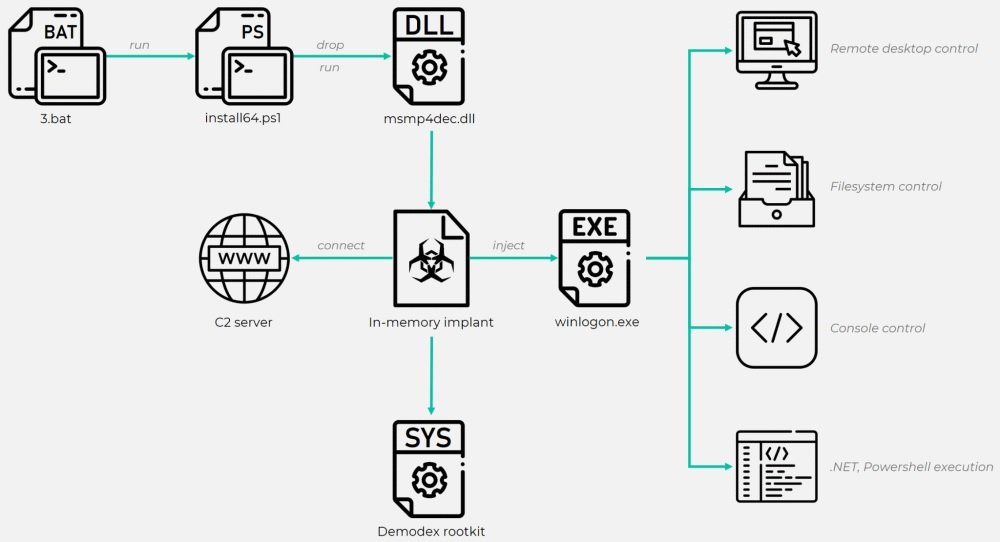
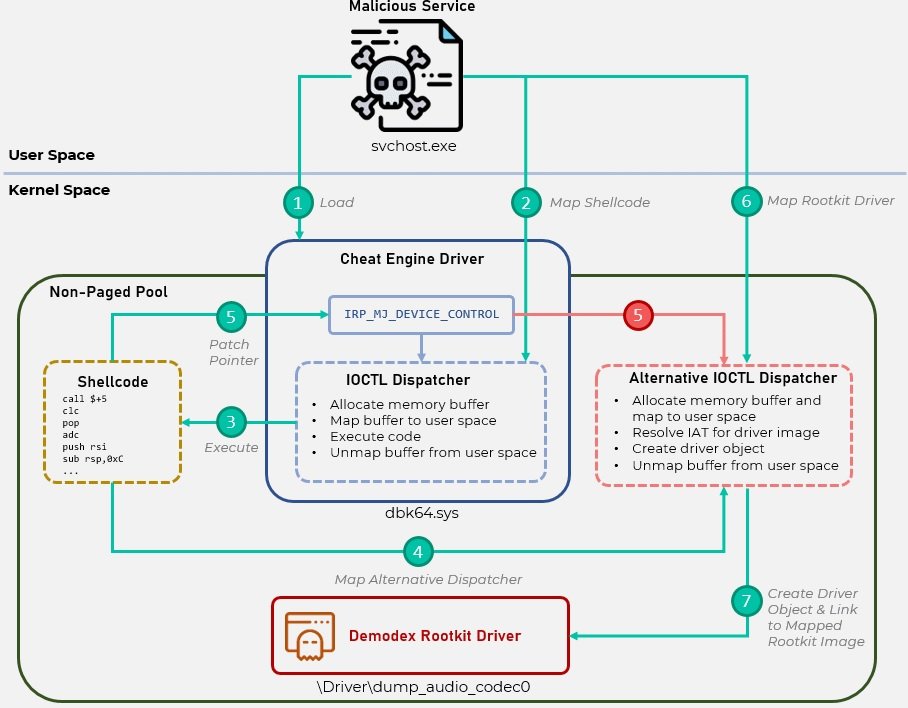
The backdoor allows hackers to download and run Cheat Engine, a tool used by some members of the gaming community to cheat in various video games. Experts point out that this group took advantage of the powerful drivers of this tool to evade the security mechanisms on Windows systems and complete the installation of the rootkit.
The rootkit, identified as Demodex, is described as an extremely advanced tool and allows threat actors to maintain access to the affected system even after a reinstallation, experts say.
Another feature of GhostEmperor is that this malware is equipped with all kinds of techniques to evade detection, which allows maintaining persistence in the affected system. The attackers resort to another ingenious trick that involves modifying communications between infected hosts and their command and control servers by repackaging the data as fake media formats.
On the other hand, security applications that detect GhostEmperor traffic would normally have classified it as RIFF, JPEG, or PNG files hosted on an Amazon server as a last trick to evade detection. While Kaspersky did not reveal the name of the affected organizations, they mention that GhostEmperor has targeted government entities and telecommunications companies in Malaysia, Thailand, Vietnam and Indonesia, in addition to isolated incidents being detected in Egypt and Ethiopia.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











