The security teams of vpnMentor, in charge of the renowned researcher Noam Rotem reported the detection of a massive data breach from the Australian firm Acquirely, dedicated to the development of marketing software. A considerable part of this company’s work is the collection of data from public sources, so the leak includes all kinds of information.
According to the report, the company stored much of this collected data in a cloud deployment without security mechanisms, so any user could have accessed the records of more than 200,000 Australian citizens.
The incident was reported on at least two occasions since September 9, although the affected company did not close access to this data until September 21, after which the CERT intervened.
The report notes that Acquirely was using an Amazon Web Services (AWS) S3 bucket to store information collected during its regular activities. These cloud deployments must be manually configured for proper protection, which the affected company seems to have completely ignored. Acquirely did not implement any security measures in its S3 bucket, leaving the content fully exposed and within reach of any user, including threat actors.
While the information collected by the company was obtained with the prior consent of the users involved, these more than 200,000 people were never told that this information would be stored in an unprotected database.
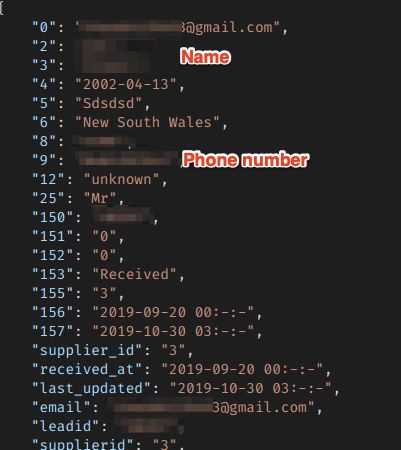
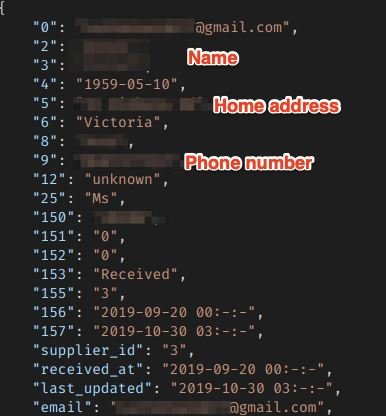
The leaking features personal identifiable information, including:
- Full names
- Email addresses
- Dates of birth
- Phone numbers
- Home and work addresses
Even though the access to this information has already been revoked, cybersecurity experts explain that it is impossible to know whether some malicious actor managed to access and further download this information for malicious purposes, so affected users are advised to be aware of any fraud attempt related to this leak. It is still also unknown if the company is directly notifying affected users.
As in any similar incident, affected users are exposed to phishing campaigns, social engineering and fraud attempts such as the well-known SIM swap, so it is essential that some kind of protection mechanism is implemented as soon as possible.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.