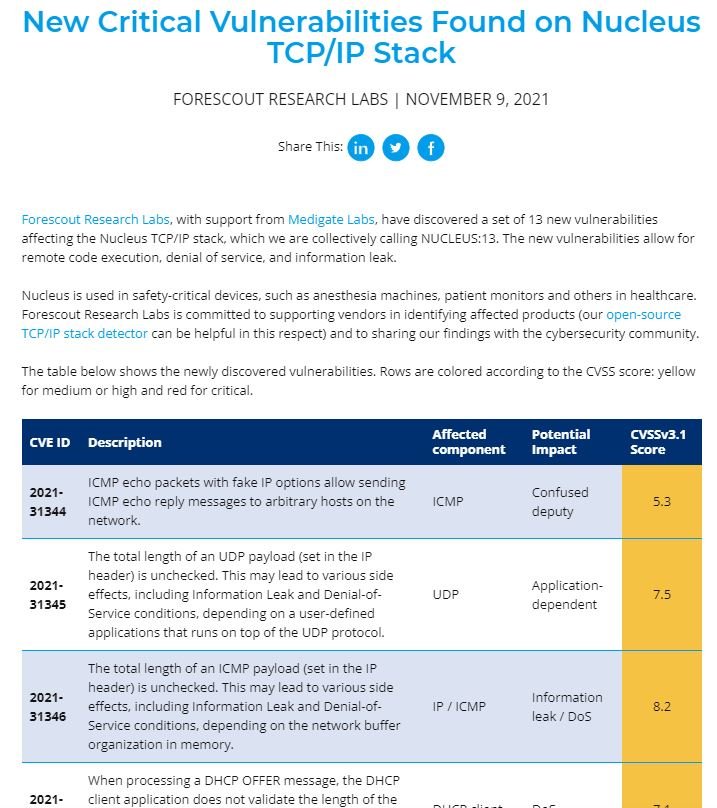
Experts recently discovered a set of critical vulnerabilities that could allow threat actors to compromise millions of Internet connected devices, including deployments used in hospitals and other critical services. Dubbed as NUCLEUS:13, this set of flaws also affects TCP/IP stacks used in Internet of Things (IoT) devices used in manufacturing, automotive development, and other relevant industries.
The finding of these flaws is part of Project Memoria, an initiative for the analysis of vulnerabilities in TCP/IP stacks used in all kinds of connected devices. Flaws could be detected in Nucleus TCP/IP stacks and their successful exploitation would allow threat actors to deploy remote code execution (RCE), denial of service (DoS) and sensitive data leakage attacks. It is not yet known whether these faults have been actively exploited.
This stack, owned by Siemens, was launched in 1993 and is used in virtually all connected devices. In hospitals, for example, this TCP/IP stack is present in heart monitors, anesthesia machines, and other critical devices.
NUCLEUS:13 involves three critical vulnerabilities, including CVE-2021-31886, which received a score of 10/10 as per the Common Vulnerability Scoring System (CVSS). This flaw resides in ftp servers, which do not properly validate the length of user commands, leading to a buffer overflow to trigger the attack.
Moreover, CVE-2021-31887 resides on FTP servers, which are unable to properly override the length of PWD or XPWD FTP server commands and CVE-2021-31888 is a vulnerability that occurs when the FTP server does not properly validate the length of MKD or XMKD FTP Commands. The two flaws received CVSS scores of 9.9/10.
While a threat actor would have to follow a long and complicated process for the successful exploitation of this flaw, the cybersecurity community considers this to be a real risk, not only for healthcare facilities, but for all kinds of industries. The good news is that Siemens has already issued security patches to address these flaws, so administrators of affected deployments are advised to upgrade as soon as possible.
In addition to installing the updates, experts recommend implementing additional security measures, especially for the protection of critical systems.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











