Specialists from the security firm Dr Web report the detection of multiple applications infected with malware in AppGallery, the official application store for Huawei devices. The apps are infected with Android.Cynos.7.origin, a variant of the well-known Cynos Trojan, and have been installed more than 9 million times.
It is worth noting that Huawei launched AppGallery after Donald Trump’s administration banned this and other Chinese tech companies in the U.S. from accessing U.S. technology, including the Android operating system. Due to this decision, all Huawei smartphones work with their own operating system and can only access the apps available in their own app store.
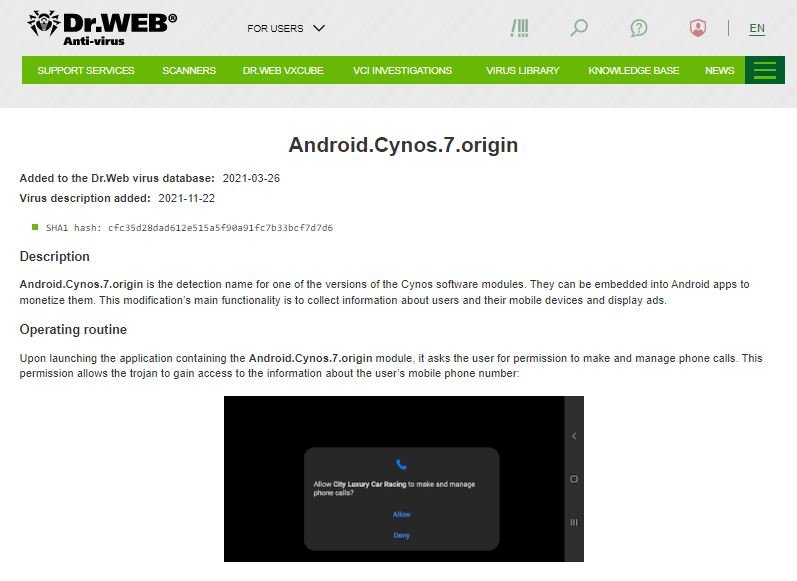
According to the experts, when installed, compromised applications require multiple permissions, including the ability to make and manage phone calls. If the user grants these permissions, apps begin collecting system data and sending it to a server controlled by the attackers, including phone number, location details, mobile operator, and other records.
Regarding the compromised apps, the researchers point out that these include emulators and mobile games of various genres, some even aimed at children and adolescents, which increases the risk of access to sensitive information. The apps also targeted a variety of nationalities by detecting language and localization settings, primarily affecting users in China and Russia.
The researchers concluded their report by listing some indicators of compromise, including shorter battery life, appearance of unknown icons, system slowdown and appearance of invasive advertising.
Upon receiving the report, Huawei decided to remove nearly 200 potentially compromised applications, in addition to new security measures for the inclusion of new software in AppGallery in the future. At the moment it is unknown if the company took any action against the developers of these applications.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











