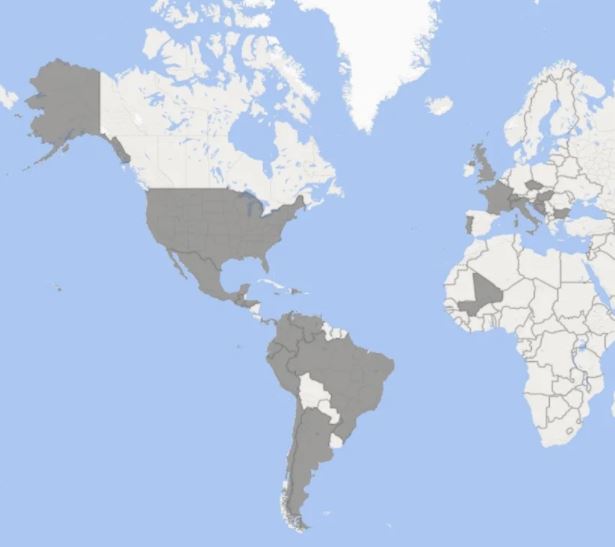
As part of an ambitious security effort, Microsoft took control of dozens of malicious sites allegedly operated by Nickel, a China-based hacking group. Apparently, these platforms were used to direct attacks against critical infrastructure in the United States and at least 28 other countries, mainly in Latin America and Europe.
Tom Burt, Vice President of Customer Security and Trust at Microsoft, said, “Nickel has focused its efforts on public and private organizations, including diplomatic entities and foreign ministries in North America, Central America, South America, the Caribbean, Europe and Africa.”
The tech giant was able to take down the hackers’ infrastructure after a U.S. court issued an order stemming from the group’s actions. This order mentions that malicious websites were to be switched to secure servers, changing authorized name servers to NS104a.microsoftintemetsafety.net and NS104b.microsoftintemetsafety.net.
Microsoft’s security teams first detected the malicious behavior in 2016, while security firms such as Mandiant say Nickel’s existence is set back to 2010. In addition, for a couple of years the presence of this group was detected in attacks against European and Latin American countries, mainly operating malware delivery campaigns for network monitoring and data theft.
Nickel’s operations are funded by Chinese government and use previously compromised third-party VPN platforms, stolen credentials in phishing campaigns, and exploits targeting undated Exchange Server and SharePoint servers.
Since the investigation began, 24 criminal cases have been drawn up against these hackers and five against their sponsors, in addition to the removal of nearly 10,000 malicious websites and more than 500,000 online platforms potentially associated with this operation have been blocked.
Microsoft has made considerable efforts in the fight against cybercrime; A few months ago, the company seized the computing infrastructure of the Necurs botnet, used by threat actors for the distribution of malware payloads, which put millions of devices around the world at risk. According to Microsoft, at its highest point of activity Necurs was able to reach more than 40 million targets in less than two months.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











