GitHub has announced the release of updated versions of its local client in order to fix two code execution vulnerabilities. The Microsoft-owned firm hopes to mitigate the risk of exploitation for affected users.
Tracked as CVE-2022-24765, the first flaw affects users working on multi-user machines where unverified users can create a C:\.git\config directory on the Windows system, where Git operations could be executed outside a repository.
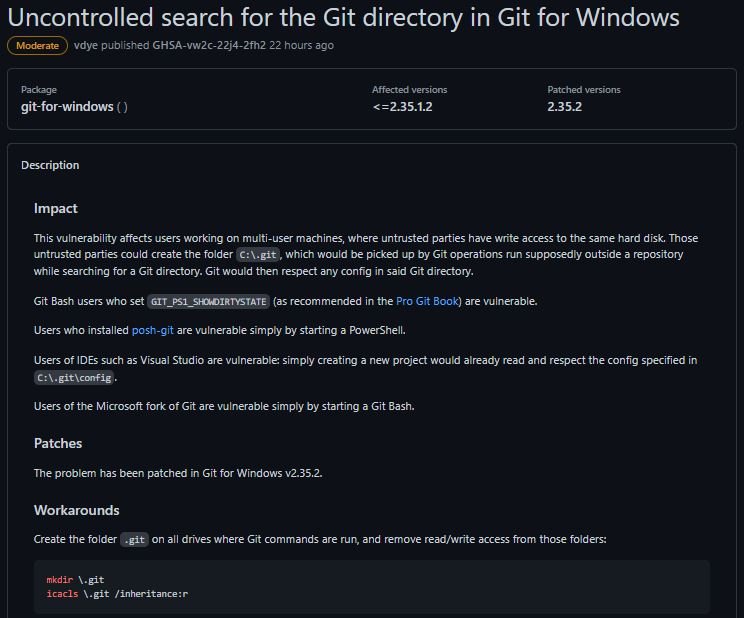
Security engineer Taylor Blau mentions, “Since some configuration variables cause Git to execute arbitrary commands, a code execution scenario could present itself when working on a shared machine.” According to the report, there are several scenarios in which a user could be affected:
- Users who installed posh-git
- Git Bash users who set up GIT_PS1_SHOWDIRTYSTATE
- IDE users such as Visual Studio
- Users of the Microsoft Git branch are vulnerable simply by starting a Git Bash
On the other hand, CVE-2022-24767 resides in the Git Uninstaller for Windows, which is vulnerable to dynamic link library (DLL) hijacking, since the high-privilege SYSTEM account inherits the settings that point to TMP and TEMP the worldwide write account C:\Windows\Temp.
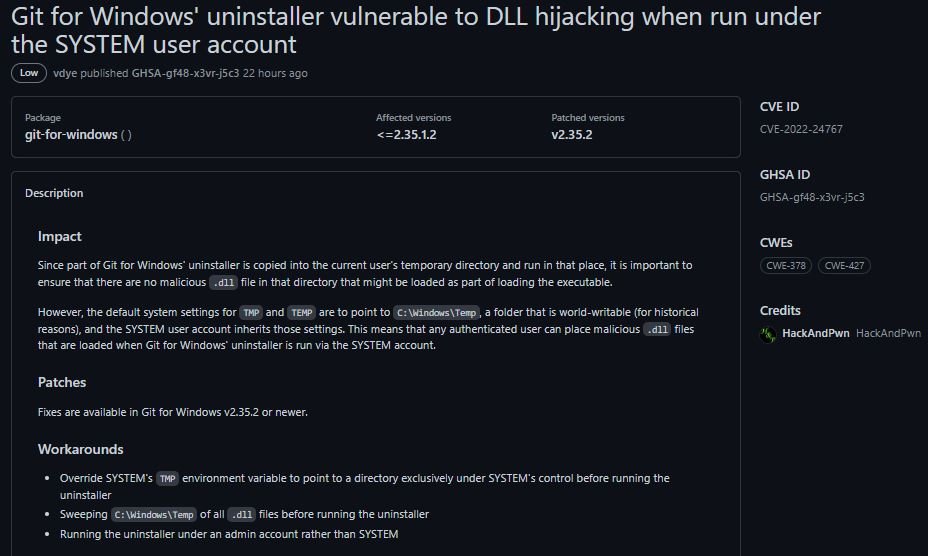
The notification for this vulnerability mentions that the default system settings for TMP and TEMP are directed to C:\Windows\Temp, so the SYSTEM user account inherits those settings; “Any authenticated user can place malicious .dll files that are uploaded when the Git uninstaller for Windows is run through the SYSTEM account,” the report states.
It should be noted that GitHub is not affected by these vulnerabilities. However, users should be aware of these vulnerabilities and update their local installation of Git, especially if they use Git for Windows or if you use Git on a multi-user machine.
The latest version of Git contains fixes for these flaws, so users are strongly encouraged to upgrade to Git v2.35.2. This version has changed its behavior when searching for a top-level .git directory, breaking down when the directory path changes ownership of the current user.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











