phpMyAdmin is a web-based application that is both open-source and free, and it was developed for the purpose of administering MySQL and MariaDB databases. phpMyAdmin is one of the most popular MySQL database management tools, with more than 200,000 downloads occurring each and every month.
It has been discovered that phpMyAdmin has a moderate security flaw that might enable malicious database operations to be carried out if an attacker were to upload a file with the extension.sql that had been carefully constructed.
An advisory that was issued by phpMyAdmin stated that “An XSS vulnerability has been discovered where an authenticated user can trigger an XSS attack by uploading a specially-crafted.sql file through the drag-and-drop interface.” This information was taken from the advisory that was issued by phpMyAdmin.
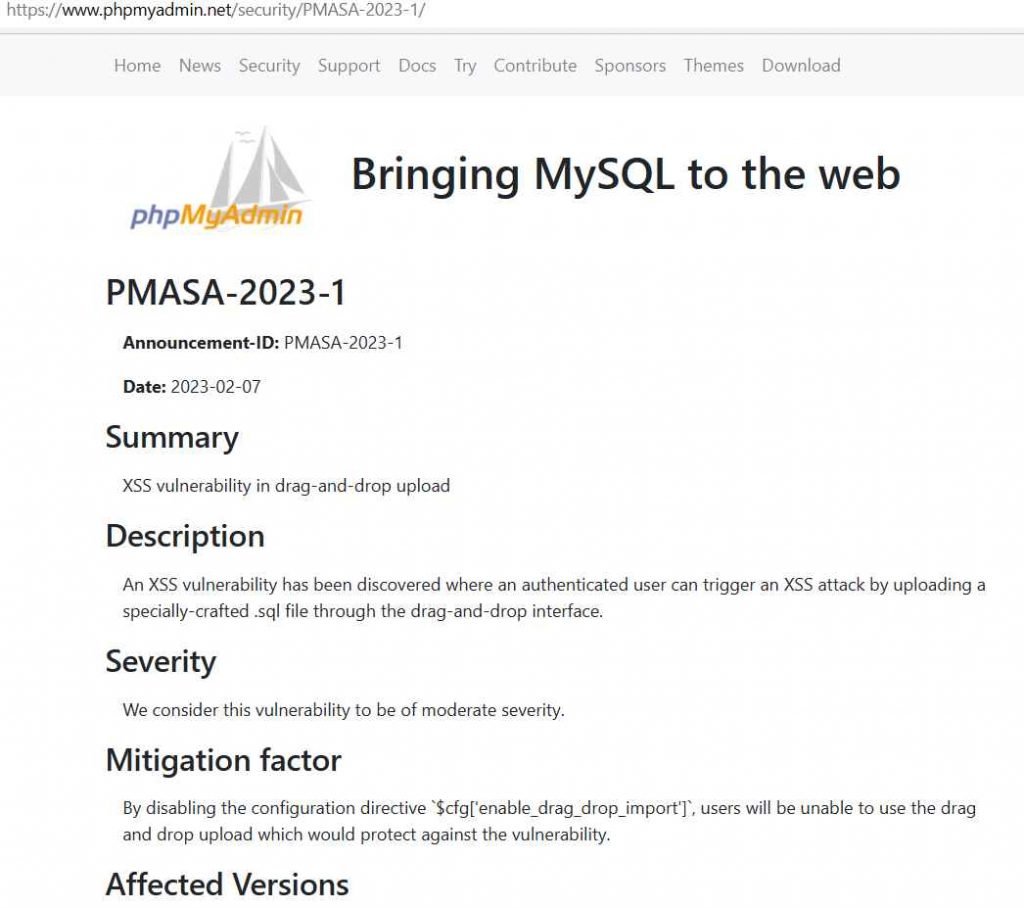
With the release of either version 5.1.2 or 4.9.11, the developers of phpMyAdmin addressed the XSS vulnerability that Erol had discovered. The risk associated with using phpMyAdmin has been rated as “moderate.” It is strongly advised that website administrators and hosting providers implement the most recent version or patch as soon as possible.
“Users will not be able to use the drag and drop upload as a result of the configuration directive ‘$cfg[‘enable drag drop import’] being disabled,” which is a measure that “would guard against the vulnerability.” Cross-site scripting (XSS) is an attack that may be used to exploit the vulnerability that was found by the security researcher Erol Guven. This attack could be used against versions of phpMyAdmin that are older than 4.9.11 and 5.2.1. The vulnerability has been there ever since version 4.3.0 was made available to users.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











