From the beginning of their existence, criminals have been abusing social networks, which have come to occupy an increasingly substantial piece of each of our lives. Threat actors may extract huge financial gains or even affect public opinion and alter the course of elections if they have access to several genuine social media accounts, which they use to spread their malicious content. At the most basic level, financially motivated organizations have established malvertising and spam campaigns as well as built up completely automated farms of content-sharing websites in order to either boost income or sell and rent hacked accounts to other bad actors.
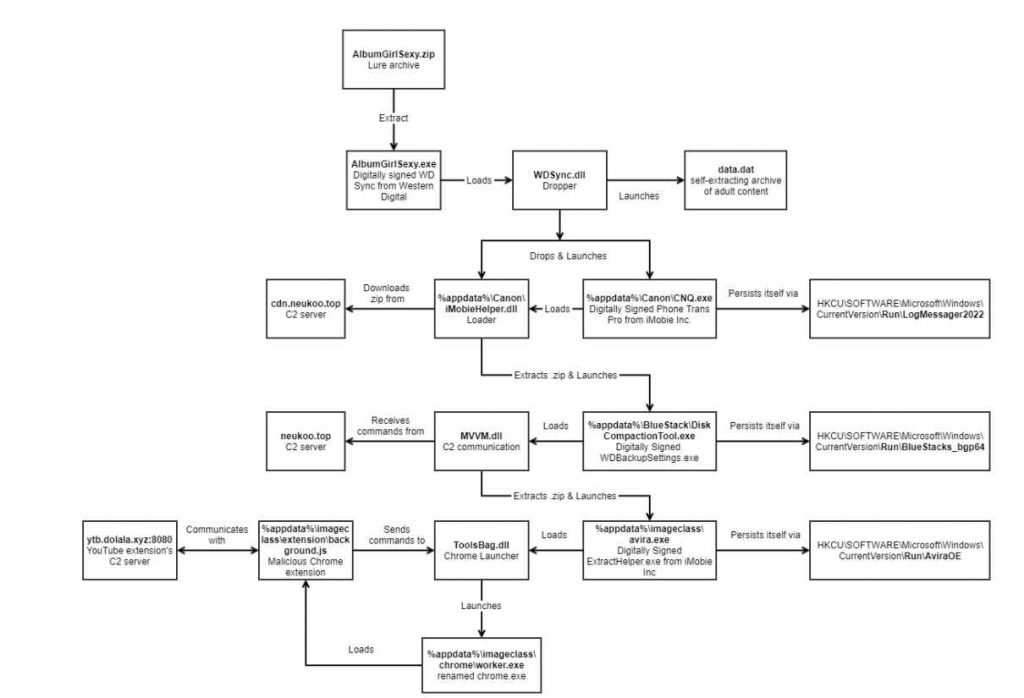
A new worldwide campaign known as S1ideload Stealer has been uncovered by Bitdefender. This campaign targets Facebook and YouTube accounts. The harmful components of S1deload Stealer are executed via DLL sideloading methods, which are relied on by the malware. It makes use of a legal executable that has been cryptographically signed, but clicking on it launches malicious code by accident.
S1deload Stealer is able to successfully infect systems due to the fact that sideloading assists in evading system defenses. Also, in order to reduce the likelihood that the user would think the executable is malicious, it goes to a genuine picture folder. Once a computer is infected with S1deload Stealer, it will steal user credentials, imitate human behavior in order to artificially boost engagement with videos and other content, determine the value of individual accounts (for example, by determining who the corporate social media admins are), mine for BEAM cryptocurrency, and spread the malicious link to the user’s followers.
Since November 2022, Sys01 Stealer has been focusing its attention on personnel working in a variety of sectors, including the government and the industrial sector, with the goal of stealing information such as passwords, cookies, and data from Facebook ads and corporate accounts.
This campaign demonstrates how threat actors are increasingly leveraging ad content to trick consumers into clicking on harmful links by employing social engineering techniques.
According to our assessment, SYS01 is a continuation of methods that are similar to those utilized by other organizations. A user should not be able to click on unchecked links or attachments on any messaging network, hence platforms that enable this should be restricted. Seen as a whole, this demonstrates how those who pose a danger adapt their methods and techniques over time and zero in on particular targets. And how difficult it may be to definitively attribute certain strains of malware to particular organizations when both the virus and the groups who employ it are in a state of perpetual change.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











