Threat actors have been relying on exploitable drivers an increasing amount in order to circumvent security measures. Drivers are low-level system components that provide access to important security structures stored in the memory of the kernel. Before allowing kernel-mode drivers to function, Windows utilizes a security technique by the name of Driver Signature Enforcement. This mechanism guarantees that the drivers have been digitally signed by a legitimate code signing authority before Windows would allow the drivers to operate. This signature acts as a trust mark to validate the authenticity of the program and to safeguard the user’s system from any potential vulnerabilities.
In order to circumvent this security precaution, attackers must either devise a method to acquire a malicious driver certified by a trustworthy certificate or engage in a BYOVD attack, in which they exploit a legal commercial software driver in order to accomplish their objective. Both of these options are very difficult to do. In contrast, the malware takes use of a genuine driver that is not up to date and may be exploited. A “bring your own vulnerable driver” (BYOVD) attack is the usual name for this kind of attack.
In this particular instance, the attackers made use of a driver that was not only developed by Microsoft but also signed by the company. The team at Sysinternals has developed a suite of administrative tools, one of which is called Process Explorer driver. This driver has a number of features that allow users to interact with processes that are currently active.
Sophos X-Ops has conducted an investigation into many occurrences over the course of the previous few months, all of which included attackers attempting to deactivate EDR clients by using a novel defensive evasion technique that we have named AuKill. In order to deactivate EDR processes on the target machine before installing either a backdoor or ransomware, the AuKill program takes use of an old version of the driver that is utilized by version 16.32 of the Microsoft application known as Process Explorer.
Since the beginning of 2023, the tool has been used in at least three ransomware instances in order to thwart the target’s protection and install ransomware. These events are as follows: In January and February, attackers utilized the program after delivering the ransomware known as Medusa Locker; in February, one attacker used AuKill just before releasing the malware known as Lockbit.
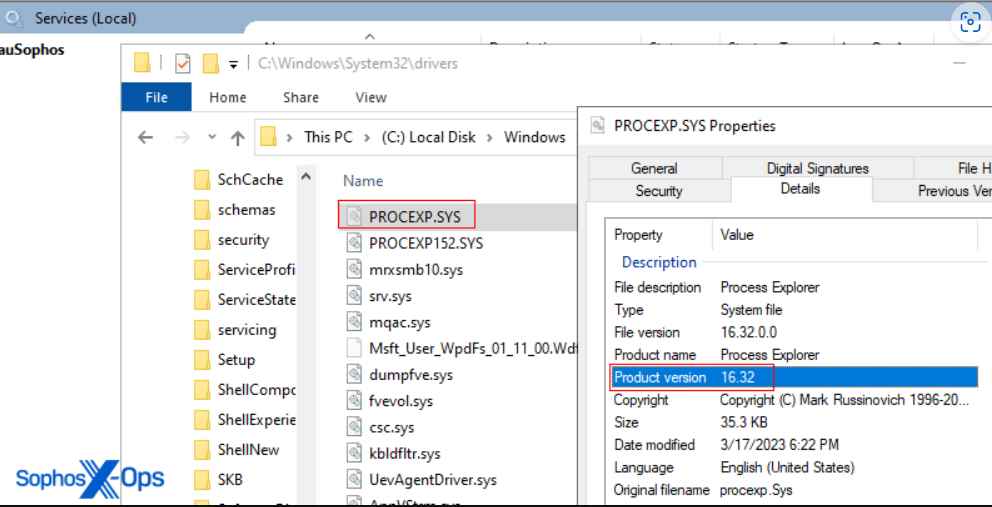
A driver with the name PROCEXP.SYS is placed in the C:\Windows\System32\drivers directory when using AuKill. This driver is from the release version 16.32 of process Explorer. The official driver for Process Explorer has the filename PROCEXP152.sys, and it is often located in the same directory as the fake driver. Both drivers may be installed on a computer at the same time if that computer is running a copy of Process Explorer. Additionally, the AuKill installer will place an executable version of itself in either the System32 or the TEMP directory, where it will operate automatically as a background service.
For instance, user-mode programs may send the IO control code IOCTL_CLOSE_HANDLE to the driver, which instructs the driver to shut a protected process handle, which ultimately results in the process being terminated.
For an attacker to successfully exploit this process, administrator rights on the target machine are required. When an attacker succeeds in gaining administrator rights, it normally indicates that the attacker now has complete control over the computer.
In order to get beyond such security measures, attackers need to go one step further and start a driver while it is in kernel mode. In this instance, AuKill circumvents these security measures by exploiting a valid driver that is used by Process Explorer.
In most cases, an EDR client is made up of a number of different parts that cooperate with one another. One example of a component is a currently-running process or an already-installed service, each of which has its own set of capabilities. Therefore, in the event that one freezes or shuts down, it often resumes as quickly as it can.
AuKill initiates several threads in order to guarantee that the EDR processes and services do not become active again, which helps avoid these components from having to be restarted. Each thread focuses on a particular component and checks in a continual manner to see whether the processes or services that it is targeting are active. AuKill will deactivate or terminate it if any of them are, if any of them are.
The practice of disabling EDR clients by utilizing drivers, whether such drivers are valid but misused for malicious purposes (BYOVD) or are issued by a certificate that was stolen or leaked, remains common among adversaries who wish to deactivate protection systems.
Over the course of the previous year, members of the security community documented many situations in which drivers were used as weapons for nefarious reasons. The finding of such a tool lends credence to the theory that adversaries are continually working to weaponize drivers.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











