Since its release in June 2022, the Play ransomware, commonly referred to as PlayCrypt, which is being developed by a group called Balloonfly, has been responsible for a number of attacks that have received significant media attention. Play, much like the majority of other ransomware gangs today, engages in double-extortion attacks. In these attacks, the attackers first remove data from the target networks before encrypting the data. Initially, the ransomware group targeted businesses located in Latin America, with a particular emphasis on Brazil; however, they quickly expanded their scope of attack.
Play is notorious for exploiting a variety of vulnerabilities, including those found in Microsoft Exchange (CVE-2022-41080 and CVE-2022-41082), in order to achieve remote code execution (RCE) and enter victim networks. The gang was also one of the first ransomware groups to use intermittent encryption, a method that enables victims’ computers to be encrypted more quickly. The strategy involves encrypting only a portion of the content of the files that are being targeted, which would still prevent the data from being retrieved.
The Play ransomware gang is making use of two new, custom-built tools that provide it the ability to enumerate all users and machines on a compromised network and copy data from the Volume Shadow Copy Service (VSS) that are ordinarily locked by the operating system. These tools were created by the Play ransomware organization.
Grixba
Grixba (Infostealer.Grixba) was the first tool discovered by researchers at Symantec. Grixba is a network-scanning program that is used to enumerate all of the users and machines that are part of the domain.
Threat actors enumerate software and services by using WMI, WinRM, Remote Registry, and Remote Services. This is accomplished with the help of the.NET infostealer. The virus searches for the presence of backup and security software, as well as remote administration tools and other applications. The information that is acquired is then saved in CSV files and packed into a ZIP file before being sent to the threat actors for later manual exfiltration.
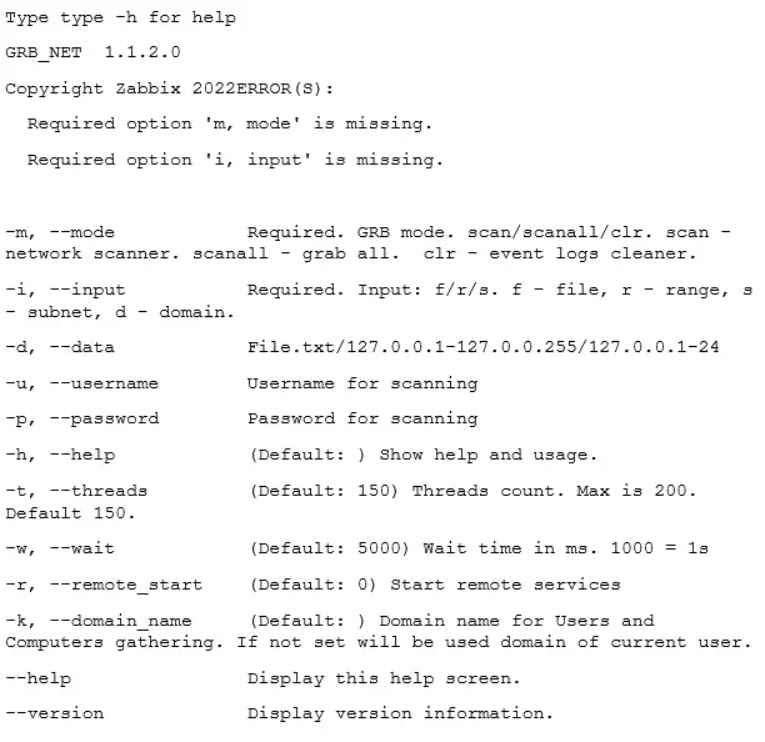
The Play ransomware group used the popular.NET programming tool known as Costura to create the Grixba ransomware. Costura allows developers to incorporate all of an application’s dependencies into a single executable file. Because of this, there is no longer a need to deploy the program and all of its dependencies in a separate operation, which makes it much simpler to both distribute and deploy the application. The DLL file costura.commandline.dll, which is used by Grixba for the purpose of command line parsing, is embedded by Costura into programs.
The VSS Copying Tool
The Play ransomware group was seen utilizing yet another.NET executable not too long ago, and this one, like the others, was produced with the help of the Costura tool.
Executables may have the AlphaVSS library built-in thanks to Costura. A high-level interface for interfacing with VSS is made available via the AlphaVSS library, which is built on top of the.NET framework. By providing a variety of regulated application programming interfaces (APIs), the library makes it simpler for.NET applications to communicate with VSS. These application programming interfaces (APIs) provide developers the ability to make, manage, and remove shadow copies, in addition to accessing information about existing shadow copies such as their size and status.
AlphaVSS is used by the program that was developed by the operators of the Play ransomware in order to copy files from VSS snapshots. The utility will go through all of the files and folders that are contained inside a VSS snapshot and then copy them to a target directory. Before the encryption takes place, the program gives the attackers the ability to copy data from VSS volumes that are located on compromised workstations. This gives the threat actors the ability to copy files that the operating system would ordinarily prevent them from copying.
Ransomware gangs are increasingly turning to the use of bespoke tools since these tools can be adapted to the surroundings of individual targets, hence making ransomware assaults both quicker and more effective. Ransomware groups preserve a competitive edge and increase their earnings by guarding the confidentiality of their own tools and limiting access to them.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











