Researchers at TrendMicro have uncovered a new risk to Docker containers, a piece of malware that they have called “TrafficStealer.” The purpose of this program is to earn income by influencing web traffic and ad interaction via the use of containers. The danger was recognized for the first time when it was discovered that one of their containerized honeypots was hosting the execution of a program that was foreign to them.
During the process of analysis, they discovered that one of those honeypots had collected a dataset; this is an uncommon occurrence given that they had not programmed the honeypots to do so. However, instead of cryptocurrency-mining software or Linux commands that were probably performing espionage, they discovered an unknown application operating in the background. This program was a container that was exploiting the laboratory network to create money by sending visitors to particular websites and interacting with advertisements. The attackers had successfully transformed the honeypot into a revenue-generating machine for themselves, but they had also left some vital information behind, which allowed them to obtain a better knowledge of their strategies and extract significant learnings from this experience. The program known as TrafficStealer functions by using a variety of methods, including site crawling and click simulation, among others. Web crawling is the process of searching the internet for websites with a high potential for advertising income, and click simulation is the generation of false clicks on advertisements that are shown on such websites. This procedure leads to a greater apparent level of engagement, which ultimately results in more ad income for the attackers. Because the server encrypts all of the traffic that is exchanged with it, the actions are suspicious.
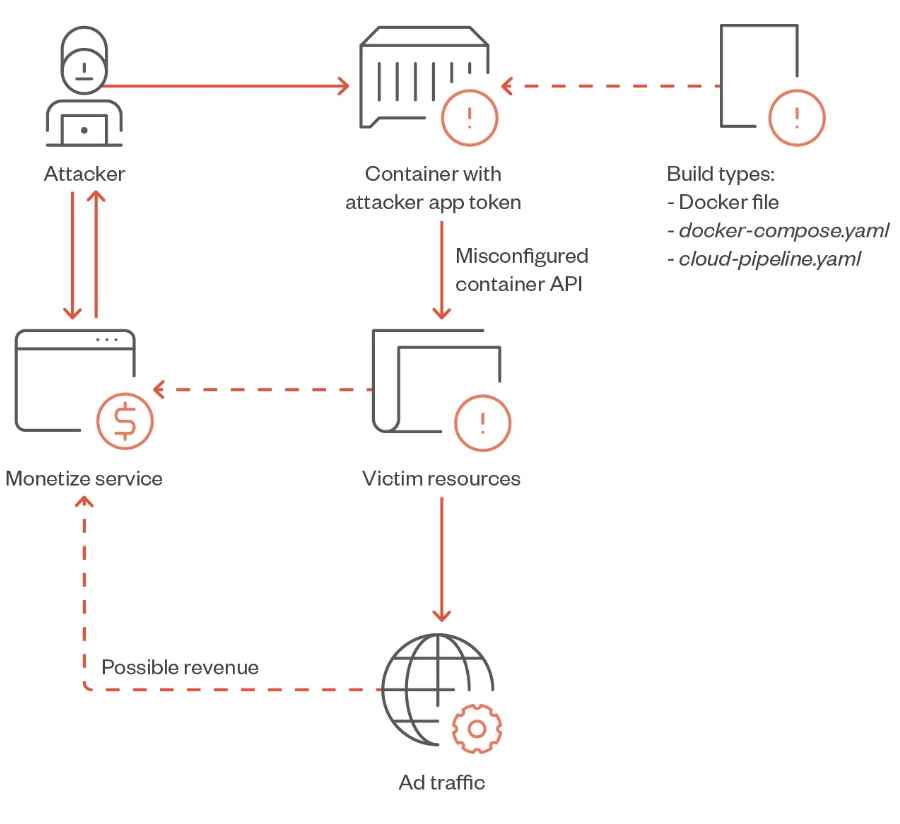
The container image that was discovered in the environment was uploaded by a service that provides something called “traffic monetization.” However, in this situation, the service offers to pay users who are willing to install the piece of software that accepts traffic from various mobile app users and proxies it through this container app. The phrase may be employed in a wider sense and indicate multiple sorts of services, but in this instance, the service promises to pay users who install the software. It is speculated that the subscriber will be compensated monetarily in exchange for the routing of the other subscriber’s network traffic via the subscriber’s very own network. Upon registering for the service, the user is provided with a one-of-a-kind token that acts as an ID. This token will thereafter be customized and utilized for the purpose of collecting any potential income.
There is no visibility on the traffic being handled by the subscriber’s device while it is being used as a proxy after the software or container belonging to the attacker has been installed or started.
The piece of software, which has been given the name “TrafficStealer,” accomplishes its goals by using a variety of operational modes. The developers assert that there is nothing unlawful in the traffic, but at the same time, they assert that they do not own any of the traffic that is created on the client. This assertion is based on the premise that victims are the ones who are operating the container and the application.
The whole of the data sent to and received from the server is encoded, and the connection takes place over an odd TCP port, both of which raise questions about the activities. Customers that are seeking to gauge how well their advertisements are doing not only have to pay for the use of their networks’ traffic but also have to deal with the unknown traffic that is being routed via their networks.
When using the official service, the user is required to register an account in order to generate a token that can be used as a parameter. Additionally, the user is required to create a one-of-a-kind ID in order to operate the service locally. The malicious actor that hacked into the system had their token hard-coded and sent along to the container setup as a parameter.
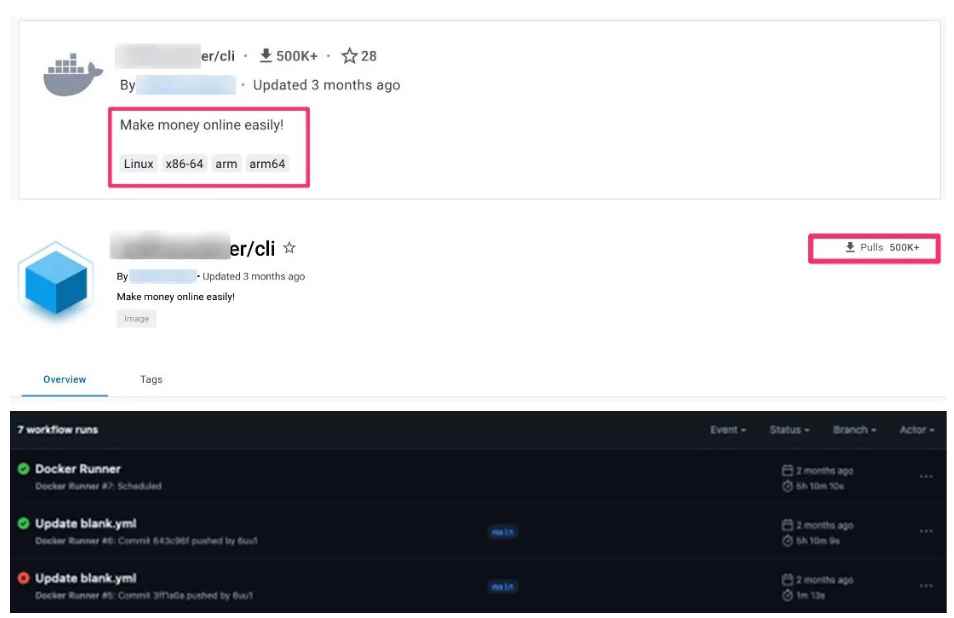
In searching for code repositories exhibiting a similar pattern of behavior, they came across instances of the same pattern in the Dockerfile and docker-compose.yaml files. Even on the YAML files used in cloud pipelines, the same behavior might be seen in certain implementations of the problem. YAML configuration files provide applications and software some degree of structure when it comes to the assignment of software settings and parameters, while the cloud pipeline makes it possible to automate the deployment, operation, and change of cloud services. In this particular scenario, the process of publishing the configuration file and automatically deploying it to the cloud was made easier by the developers and publishers of these YAML files by automating the process. As a consequence, this leads to a quicker deployment of malicious services, more automation, and, most crucially, increased attack scale. Given these files and behaviors, the amount of revenue received by the attacker will increase proportionally with the number of runners that are deployed.
The image that was used to infect the honeypot was downloaded 500,000 times from Docker Hub alone, which resulted in 15 MB of data being processed in a couple of seconds. The discovery of this containerized version of TrafficStealer demonstrates how threat actors modify their tactics in order to make the most of emerging platforms and popular software. There is a possibility that some of the customers who are aware of this service and who are ostensibly benefiting from it are not really reaping the returns that were promised on capital costs such as the original membership fee that they paid for cloud services. On the other hand, it’s possible that some people are blindly running it and making income for the attackers without even realizing it. This suggests that there will be reductions in the fees collected for cloud services. In addition, the users did not provide permission for the piece of software to operate on their individual environments (in particular as a PUA), and as a result, it is quite probable that they do not have any control over the traffic that utilizes the network as a proxy. In the event that the network is being used for illegal actions, the IP address of the person or organization that is using it without their knowledge is the one that is recorded.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











