Researchers from VulnCheck have created a new attack for the previously discovered serious issue in PaperCut servers. This exploit, which is tagged as CVE-2023-27350 and has a CVSS score of 9.8, is able to avoid detection by any of the existing countermeasures. The vulnerability, identified as CVE-2023-27350 and with a CVSS score of 9.8, affects PaperCut MF and NG installations and may be abused by an unauthenticated attacker to execute arbitrary code with SYSTEM privileges. The problem is tracked as CVE-2023-27350. Despite the fact that the Australian company patched the vulnerability on March 8, 2023, the first signs of active exploitation didn’t appear until April 13, 2023.
Since then, several threat organizations, including ransomware attackers, have leveraged the vulnerability, and further post-exploitation activity has resulted in the execution of PowerShell instructions meant to deliver additional payloads.
Now, VulnCheck has released a proof-of-concept (PoC) exploit that is able to circumvent previously established detection signatures. This is accomplished by taking advantage of the fact that “PaperCut NG and MF offer multiple paths to code execution.”
The researchers have made public a proof-of-concept attack that executes code in a manner that is distinct from any of the previously released detections.
According to the researchers, there are just two public exploit variations that are accessible to the public:
Exploits that execute Windows instructions by using the PaperCut print scripting interface (variations on the Horizon3.ai vulnerability).
Exploits that make advantage of the print scripting interface in order to release a malicious JAR (for an example, check this pull request for Metasploit).
Both of these approaches, as the specialists pointed out, exploit the built-in JavaScript interface of the system.
“Rhino is the JavaScript engine, and in addition to that, it gives users the ability to run arbitrary Java code.” According to VulnCheck, “PaperCut Software implemented configuration options to reduce the risk of this arbitrary code execution vector; however, because the attacker has full administrative access, those protections are easily disabled.”
At the moment, there are three distinct kinds of detections, each of which is separately based on either Sysmon (for example, process creation analysis), log file analysis, or Network signatures.
The researchers showed how to take advantage of the vulnerability by misusing the “User/Group Sync” function.
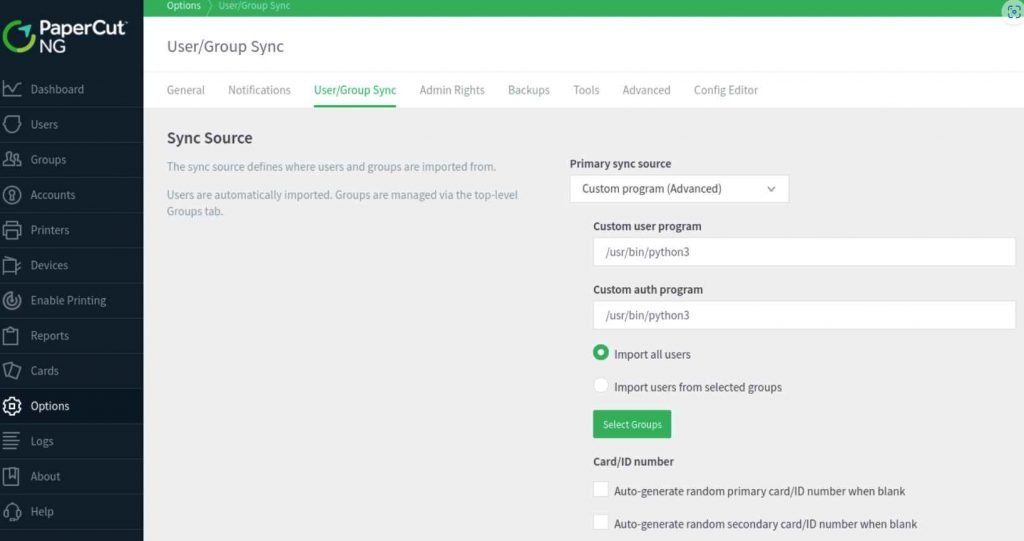
The proof-of-concept attack that was developed by VulnCheck changed the auth program on Linux to “/usr/sbin/python3,” while on Windows it changed it to “C:WindowsSystem32ftp.exe.” When attempting to log in to a vulnerable server, threat actors can execute arbitrary code on the server by providing a malicious username and password combination. Without triggering any of the known detections, the attack approach could be used to either download a custom reverse shell hosted on a remote server on Windows or run a Python reverse shell on Linux. Both of these actions could be performed without the need for administrator privileges.
According to the information provided by VulnCheck, an administrator user targeting PaperCut NG and hackers may use numerous different routes to execute arbitrary code.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











