Hackers working for the Russian government disguised as technical support personnel on Microsoft Teams in order to breach the security of hundreds of businesses throughout the world, including government entities.
Microsoft security experts said on Wednesday that a Russian state-sponsored hacking outfit named by Microsoft as “Midnight Blizzard,” but more generally known as APT29 or Cozy Bear, was responsible for the “highly targeted” social engineering attack.
APT29 hackers started attacking sites at the end of May, and they created new domains with a technical help theme by using accounts for Microsoft 365 that had been hijacked in earlier attacks. By using these domains, the cybercriminals sent messages via Microsoft Teams that were designed to trick users into giving acceptance for multifactor authentication prompts. The hackers’ ultimate goal was to get access to user accounts and steal critical information.
The actor utilizes Microsoft 365 tenants that belong to small companies that they have previously infiltrated in other attacks in order to host and launch their social engineering attack. This helps the actor carry out their attack more easily. The malicious actor first renames the compromised tenancy, then establishes a new onmicrosoft.com subdomain, and then installs a new user linked with that domain from which to deliver the outbound message to the target tenant. In order to provide the impression that the communications are legitimate, the bad actor creates a new subdomain and a new tenant name by using keywords with a product name or security-related topic. Their investigation is still continuing, and it includes looking at these precursory attacks that were aimed at compromising legal Azure tenants as well as the use of homoglyph domain names in social engineering lures. Microsoft has taken precautions to prevent the perpetrator from making use of the domains.
Chain of attacks using social engineering
Within the context of this activity, Midnight Blizzard has either obtained valid account credentials for the users they are targeting or they are targeting users who have passwordless authentication configured on their account. In either case, it is necessary for the user to enter a code that is displayed during the authentication flow into the prompt on the Microsoft Authenticator app that is installed on their mobile device.
When a user tries to log in to an account that requires this kind of MFA, they are shown a code that they must input into their authenticator app. This happens after the user has already attempted to authenticate themselves to the account. The user is presented with a popup on their device asking them to enter a code. After that, the actor will send a message to the user who is being targeted using Microsoft Teams, requesting that the user input the code into the prompt that is shown on their device.
The first step is for teams to request to speak.
It’s possible that an external user posing as a member of the security or technical support team will send a message request via Microsoft Teams to the user who is the target.
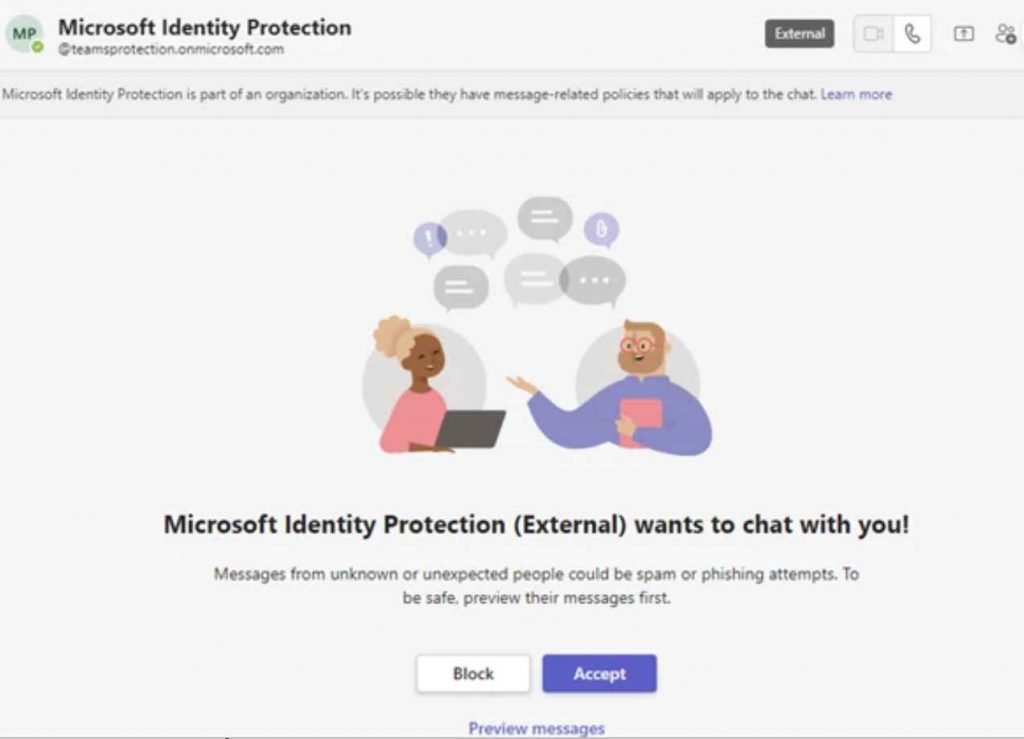
The second step is to request authentication from the app.
If the target user accepts the message request, they will then get a message from the attacker in Microsoft Teams. In this message, the attacker will try to persuade the user to input a code into the Microsoft Authenticator app that is installed on their mobile device.

Third Step is Authentication with the MFA Completed Successfully
The threat actor will be provided a token to authenticate as the targeted user if the targeted user accepts the message request and inputs the code into the Microsoft Authenticator app. Following successful completion of the authentication process, the actor is granted access to the user’s Microsoft 365 account.
After that, the actor will continue to perform post-compromise behavior, which will often entail the theft of information from the Microsoft 365 tenant that was hacked. It is probable that the actor is attempting to overcome conditional access controls that have been defined to limit access to certain resources to managed devices only by adding a device to the organization as a managed device through Microsoft Entra ID (previously Azure Active Directory). This occurs in some instances.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











