PHP is a widely used programming language that is put to use in the production of dynamic web pages. On the other hand, much like any other program, it is not completely safe from security flaws. CVE-2023-3823 and CVE-2023-3824 are the names of two new security flaws that have been identified in PHP during the course of the last several months.
CVE-2023-3823 (score of 8.6 on the CVSS scale): Information Disclosure
An information disclosure vulnerability known as CVE-2023-3823 exists in PHP applications and makes it possible for a remote attacker to access sensitive data stored inside such applications. Inadequate validation of the XML input given by the user is the root cause of the vulnerability. This vulnerability might be exploited by the attacker by having them transmit a specially designed piece of XML code to the program. The program would then proceed to parse the code, at which point the attacker would be able to obtain access to sensitive information such as the contents of arbitrary files on the system or the results of queries made to external sources.
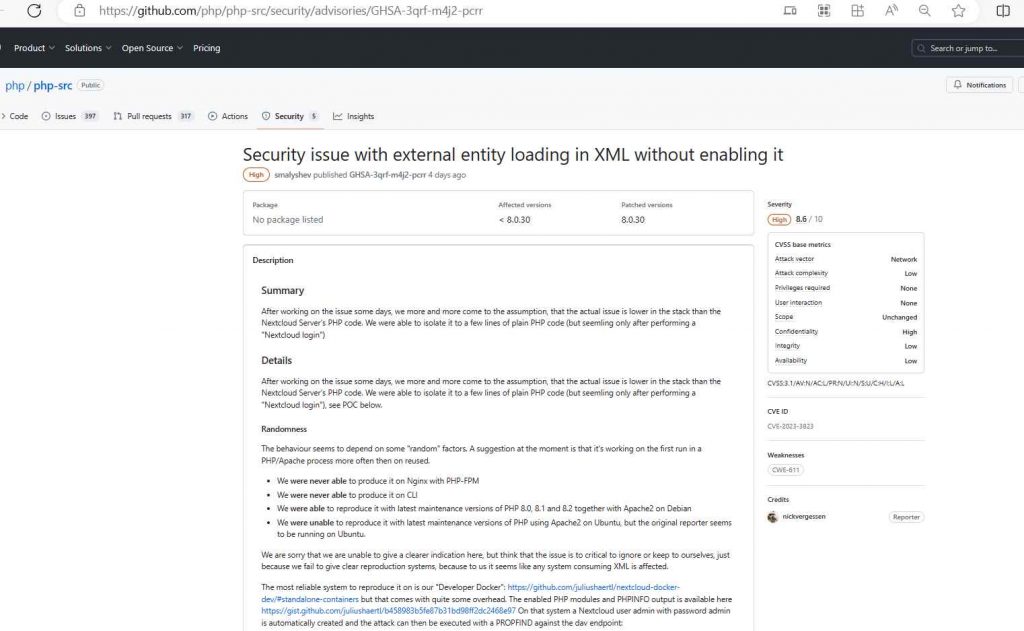
This issue may affect any program, library, or service that interacts with XML documents in any way, including processing or communicating with them. Because to the hard work done by nickvergessen, a security researcher, who also released the proof-of-concept.
CVE-2023-3824 is a buffer overflow vulnerability that has a CVSS score of 9.4.
A remote attacker might execute arbitrary code on a PHP system if they exploited the buffer overflow vulnerability known as CVE-2023-3824. This issue is tracked by the CVE identifier. The insufficient bounds checking performed by the phar_dir_read() method is the root cause of the vulnerability. By submitting a request to the application that has been carefully designed, an adversary might take advantage of this vulnerability. The request would then result in a buffer overflow, which would give the adversary the ability to take control of the system and run whatever code they pleased.
The difficulty of exploiting this vulnerability stems from the fact that it involves a number of faulty checks and overflows. For instance, it was discovered that the condition “to_read == 0 || count ZSTR_LEN(str_key)” was flawed and should not have been used. This has a number of repercussions in the code, one of which is that there is a problem with the line ((php_stream_dirent *) buf)->d_name[to_read + 1] = ‘0’;. This piece of code has the potential to overflow, and it does not NUL-terminate the filename in the correct manner. The issue has been compared to a stack information leak as well as a buffer write overflow, which only serves to exacerbate the situation.In addition to that, there may be potential worries over a buffer overflow in the memset. Even though there have been no such occurrences detected inside PHP itself, third-party extensions might still be impacted.
Although the exploitation is certainly difficult and is contingent on the particular application that is being targeted, it is nevertheless theoretically possible. According to the alert issued by the security team, “People who inspect the contents of untrusted phar files could be affected.”
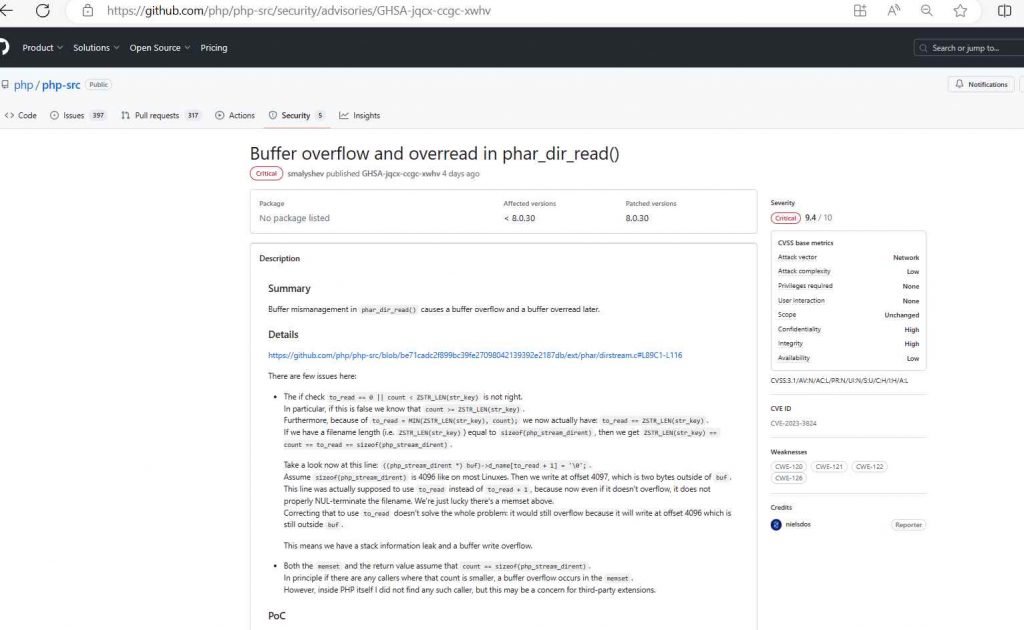
The proof-of-concept was also released thanks to the efforts of security researcher nielsdos, who is credited for his work.
In PHP 8.0.30, the vulnerabilities CVE-2023-3823 and CVE-2023-3824 have also been addressed. If you are still using an earlier version of PHP, you should consider upgrading as soon as you can to the 8.0.30 release.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











