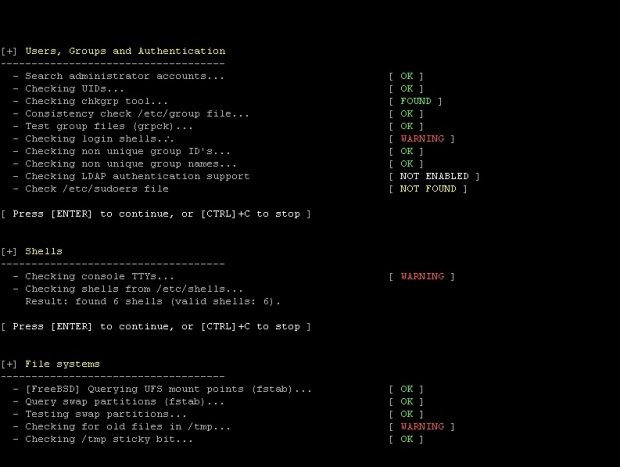
MEGA Chrome extension was hijacked to steal personal information
If you use this extension for the Chrome browser, it is recommended to uninstall it immediately Ethical hacking experts report that the official Chrome extension for the MEGA cloud storage service wouldRead More →