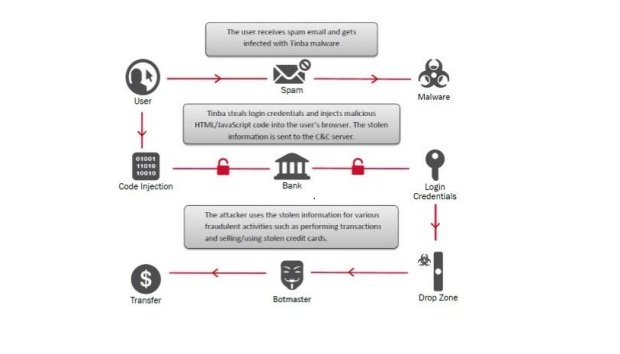
Tinba, a 20KB trojan that scares banks in Singapore and Indonesia
A new variant of the infamous Tinba banking trojan has emerged in the wild and is targeting financial institutions in the Asia Pacific region. Even small threats can scare theRead More →