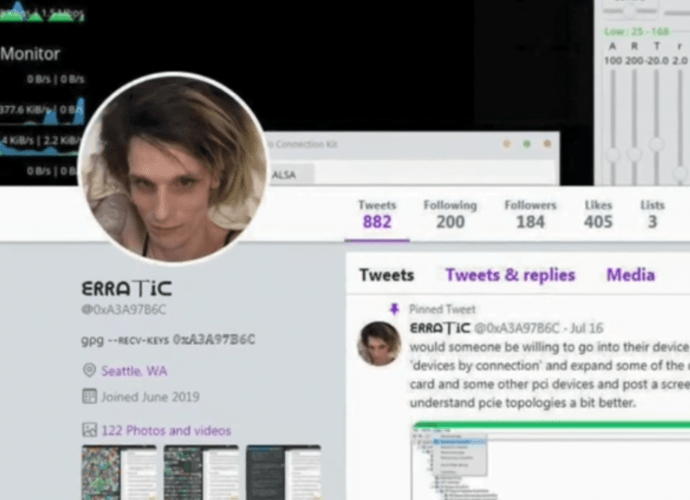
100 million Capital One customers hacked by this girl
Although legislation in various parts of the world has become much tighter on the protection of confidential information, multiple companies remain highly vulnerable to data breach incidents, affecting millions ofRead More →