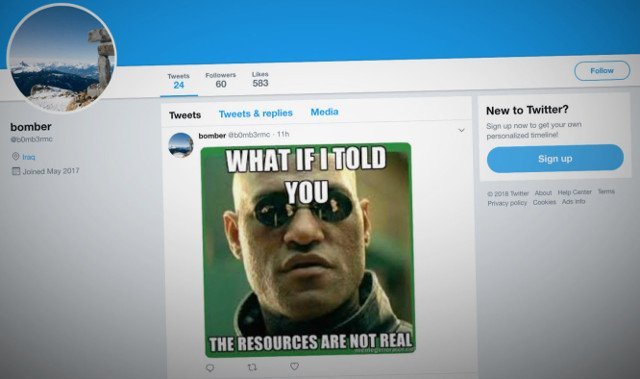
Hackers used memes posted on Twitter to control malware
A team of researchers has discovered a new way to hide malicious software The investigators of a cybersecurity firm reported the discovery of a new malware sample capable of retrievingRead More →