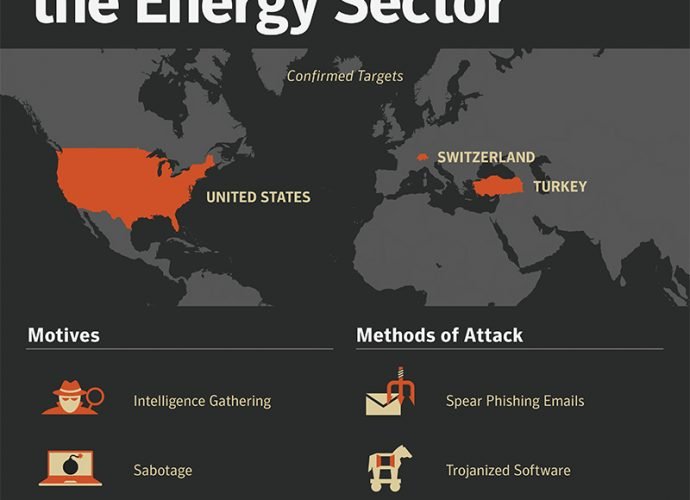
Sabotage Warning Issued on Hackers Hiding Deep Inside Energy Sector
US cyber-security firm Symantec has issued a warning today against a group of nation-state hackers that have managed to infiltrate several US and European energy firms, and are now inRead More →