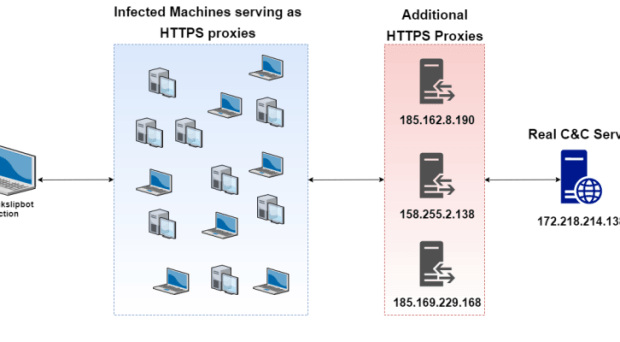
South Korean Web Hosting Provider Pays $1 Million in Ransomware Demand
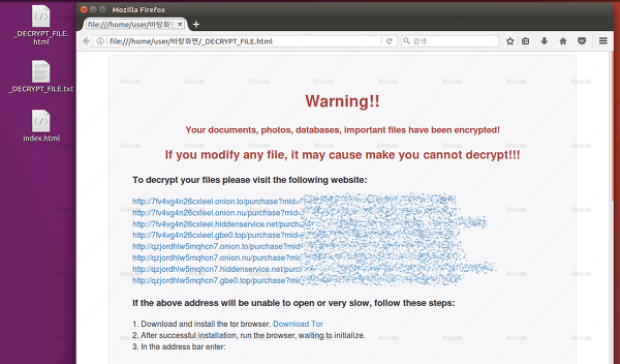
Nayana, a web hosting provider based in South Korea, announced it is in the process of paying a three-tier ransom demand of nearly $1 million worth of Bitcoin, following aRead More →