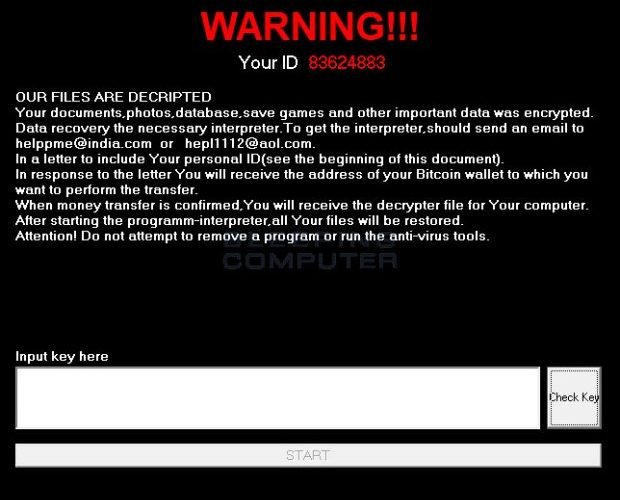
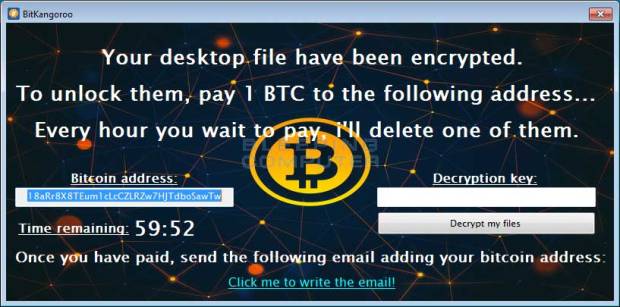
Edge Security Flaw Allows Theft of Facebook and Twitter Credentials
Argentinean security researcher Manuel Caballero has discovered another vulnerability in Microsoft’s Edge browser that can be exploited to bypass a security protection feature and steal data such as passwords fromRead More →