New LLTP Ransomware Appears to be a Rewritten Venus Locker
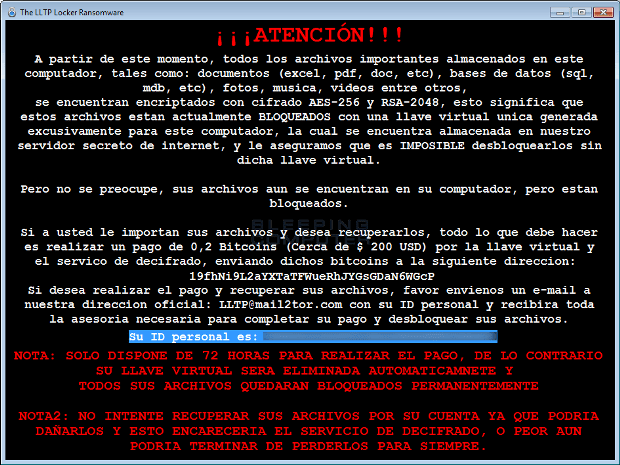
A new ransomware was discovered today by MalwareHunterTeam called LLTP Ransomware or LLTP Locker that is targeting Spanish speaking victims. On a closer look, this ransomware appears to be a rewritten version ofRead More →