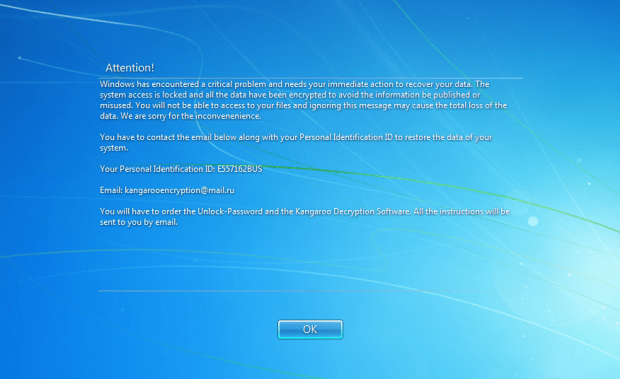
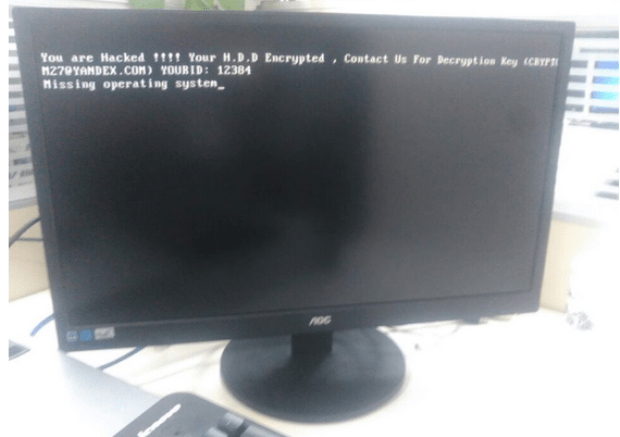
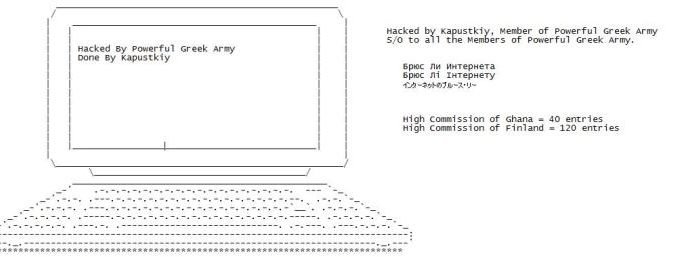
The Kangaroo Ransomware not only Encrypts your Data but tries to Lock you out of Windows
The Kangaroo ransomware is the latest ransomware from the developer behind the Apocalypse Ransomware, Fabiansomware, and Esmeralda. What makes this version stand out a bit more is the use ofRead More →