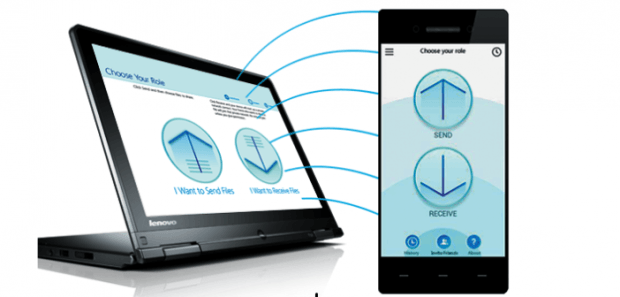
SHAREit for Windows and Android Vulnerabilities
Lenovo Security Advisory: LEN-4058 Potential Impact: Remote browsing of file system, unauthorized access of transferred files and denial of service attack that could crash the Windows SHAREit client Severity: Medium Summary: Vulnerabilities wereRead More →