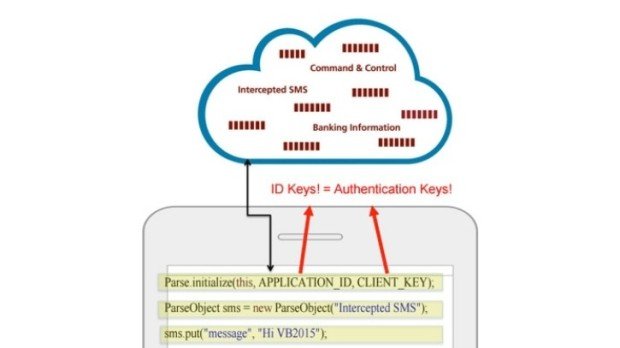
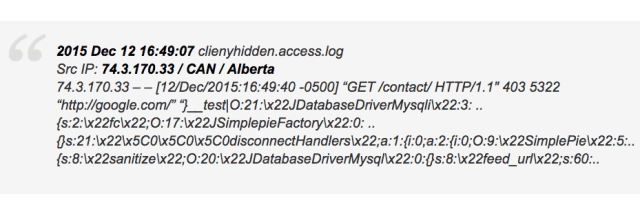
Two Mobile Banking Trojans Used Facebook Parse as C&C Server
Attackers carry out SMS fraud via the infected phones. The Android/OpFake and the Android/Marry malware families, two banking trojans targeting mobile devices, have (improperly) stored their C&C servers inside Facebook Parse,Read More →