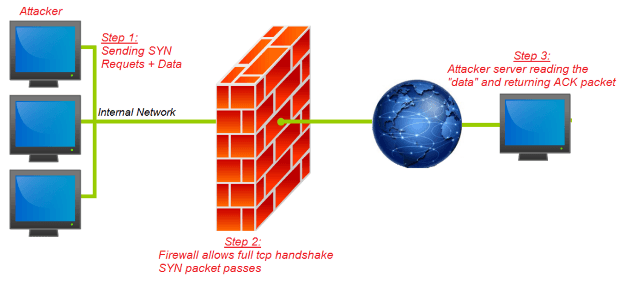
FireStorm: Severe Security Flaw Discovered in Next Generation Firewalls
BugSec Group and Cynet discovered a severe vulnerability in Next Generation Firewalls. Head of Offensive Security Stas Volfus uncovered the vulnerability, code-named FireStorm, which allows an internal entity or maliciousRead More →