Vulnerability allowed hackers to hijack active user sessions.Microsoft Exchange Server has been recently patched to fix an important security vulnerability which would have allowed attackers to gain access to active Webmail sessions via an easy to exploit flaw.
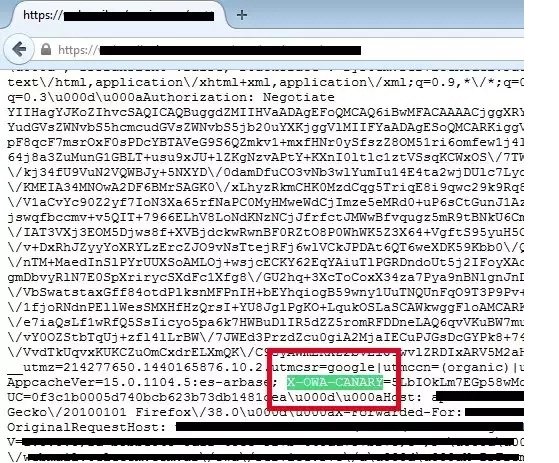
The vulnerability was found in Outlook Web Access (OWA) in Microsoft Exchange Server 2013, and allows any attacker to force the Microsoft Exchange Server to dump debug data on the screen by accessing a maliciously crafted URL.
By sifting through the information shown on the screen, attackers would have been able to obtain previously inaccessible cookie session info.
This data could then be used to authenticate against the Exchange Server’s OWA service, and gain access to an active Webmail session.
This would then allow the attacker to exfiltrate sensitive and private information from a previously secure system.
According to the National Vulnerability Database entry, this vulnerability had a low complexity level and allowed any attacker with network access to the server to employ it in their hacking arsenal.
The vulnerability (CVE-2015-2505) has been fixed by Microsoft in MS15-103.
This is not the first time this month when a vulnerability has been fixed in one of Microsoft’s Office server products. We previously reported on a XSS vulnerability found in SharePoint 2013, which allowed attackers to store attack vectors on a SharePoint server by entering malicious code in various unsanitized form fields.
Source:https://news.softpedia.com/

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











