A new ransomware called KimcilWare has been discovered that appears to be targeting web sites using the Magento eCommerce solution. It is currently unknown how these sites are being compromised, but victims will have their web site files encrypted using a Rijndael block cipher and then ransomed for anywhere between $140 USD and $415 USD depending on the variant that infected them. Unfortunately, at this time there is no way to decrypt the data for free.
KimcilWare was first spotted when a security researcher going by the Twitter handlemalwareforme had posted about a new Windows ransomware. This ransomware was a Hidden Tear variant that was broken due to SSL connectivity issues with their Command & Control server. The ransom note, though, contained the email address tuyuljahat@hotmail.com, which security researcher MalwareHunterTeam discovered also appeared on a web site that appeared to be infected with a ransomware called KimcilWare.
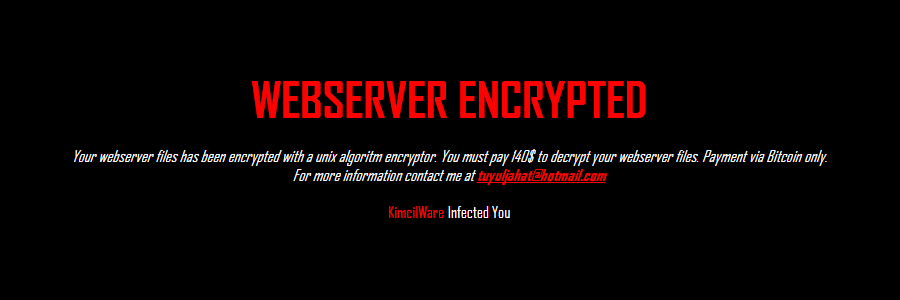
Further research turned up two support requests where people were asking for help after discovering their server was encrypted. Though there were differences between these two cases, the one similarity was that both ransom notes contained the tuyuljahat@hotmail.com email address and both were web sites using the Magento platform.
After doing some research, it is apparent that this tuyuljahat actor has been hacking Magento servers for at least the past month and installing a script that encrypts the data on the web site. When attacking the sites they they have used at least two different scripts to encrypt the data.
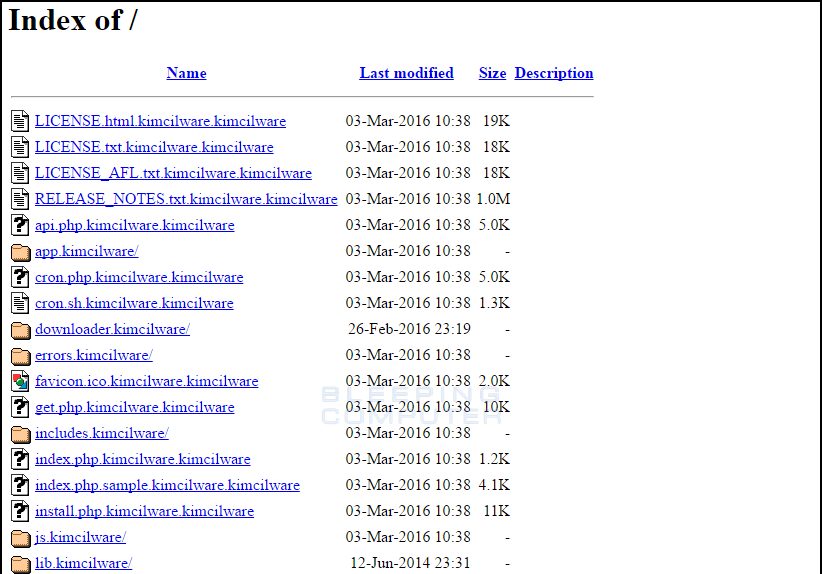
One script will encrypt all data on the web site and append the .kimcilware extension to all encrypted files. It will also insert a index.html file that displays the ransom note shown above. The KimcilWare variant has a ransom amount of $140 USD. You can see an example of a folder encrypted with the KimcilWare script below.
The other script will append the .locked extension to encrypted files, but does not replace the index.html with a ransom note. Instead it will create a file called README_FOR_UNLOCK.txt in every folder, which contains the ransom instructions below.
ALL YOUR WEBSERVER FILES HAS BEEN LOCKED
You must send me 1 BTC to unlock all your files.
Pay to This BTC Address: 111111111111111111111111111111111
Contact tuyuljahat@hotmail.com after you send me a BTC. Just inform me your website url and your Bitcoin Address.
I will check my Bitcoin if you realy send me a BTC I will give you the decryption package to unlock all your files.
Hope you enjoy 😉
The ransom amount of the Locked version is 1 bitcoin or approximately $415 USD.
At this point there is no information on how the servers are being hacked, though one victim felt it was related to the Helios Vimeo Video Gallery extension. This has not been confirmed.
Source:https://www.bleepingcomputer.com/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











