A security researcher named Casey Smith published an article last week where he detailed how the Windows Regsvr32.exe command could be used to bypass AppLocker restrictions. In this article he described a not commonly known feature where Regsvr32 can execute specially crafted scripts on a remote host using a URL. These scripts are XML files that contain embedded Jscript or VBScript scripts that will be executed when Regsvr32 runs the script.
This obviously leads to a whole mess of possibilities where an attacker can do very bad things to your computer as long as they have access to it. Unfortunately, there are many ways for an attacker to gain access to a computer, whether it be through an exploit kit or a vulnerability.
Regsvr32.exe installing Ransomware through JScript
As a test, I decided to take a ransomware javascript installer and modify it so that it can work with Regsvr32.exe. As the Nemucod ransomware relies heavily on Javascript to install itself, I thought that this ransomware would be a good one to test with.
Using the instructions found in Casey Smith’s article, I created a specially crafted XML file that contained the Javascript from the Nemucod installer. I had to modify it a bit to get it to work properly with Regsvr32.exe, but that was easy enough to do. I then modified it further by adding a small script that creates a batch file in the %Temp% folder that is executed by the script before installing the ransomware. This batch file will terminate known anti-malware and anti-virus programs so that they are unable to block the ransomware from being installed.
Unfortunately, the test worked perfectly. Regsvr32.exe was able to execute my script using a URL to my test server. This script then terminated my running anti-virus software and installed the ransomware. In order to demonstrate this test, I created the video below that shows how I used Regsvr32.exe to install the Nemucod ransomware.
What makes this method worse, is that this can be used to easily modify the system before installing a malware. Using normally white listed programs, a VBScript or JScript script can easily make registry or system configuration changes, terminate security processes, and then install whatever malware they want. Furthermore, since Regsvr32.exe is a legitimate application and these remote script files can be named whatever you want, anti-virus software will not easily detect it.
Blocking Regsvr32.exe from making outbound Requests
Unfortunately, Microsoft has remained silent regarding Regsvr32’s ability to execute scripts from a remote URL. As it is not known whether this will be patched or not, it is important to block Regsvr32.exe’s access to the network through a software firewall. If you do not have a firewall installed that can block an executable from reaching the Internet, you can use the Windows Firewall to do this.
To create this rule, click on the Start Menu and type Windows Firewall. When the Windows Firewall with Advanced Security option appears, click on it. This should open the Windows Firewall. Now click on the Outbound Rules category and then click on the Action menu and select New Rule.
You will now be in the Add Outbound Rule wizard as shown below.
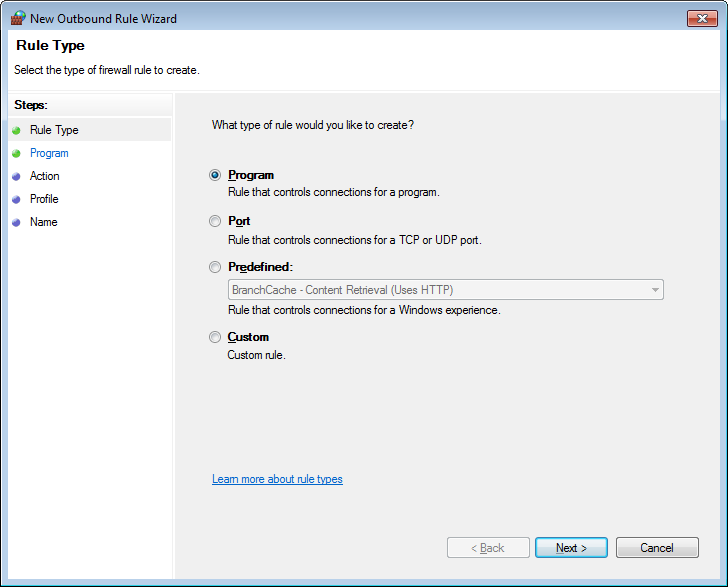
Keep the Program option selected and click on the Next button. You will now be at the screen where you select the program.
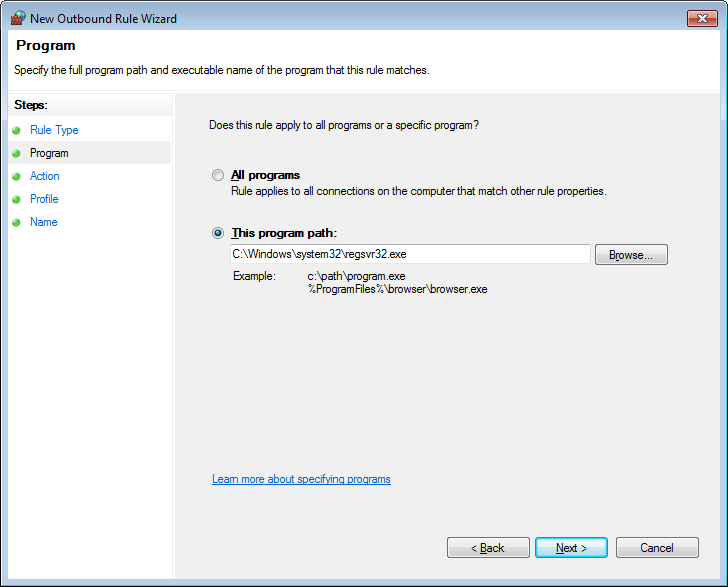
In the program path field enter C:\Windows\System32\regsvr32.exe and press the Next button. You will now be at the Action screen.
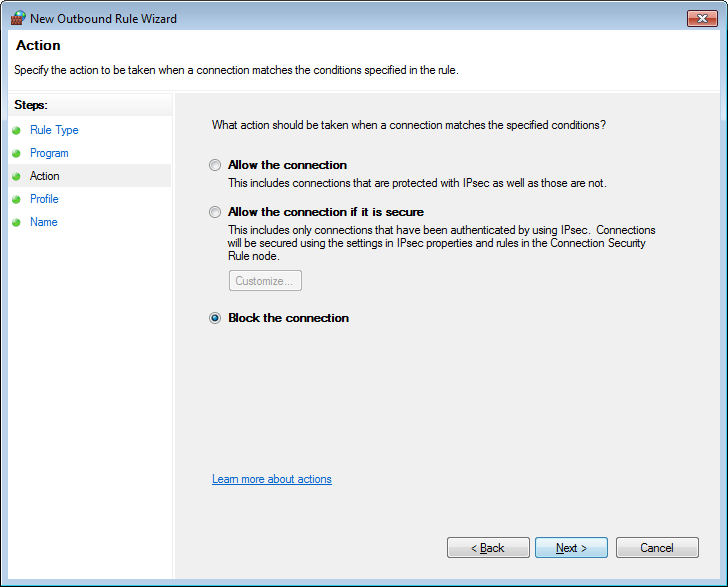
Keep Block the connection option selected and click on Next. You will now be at the profiles screen.
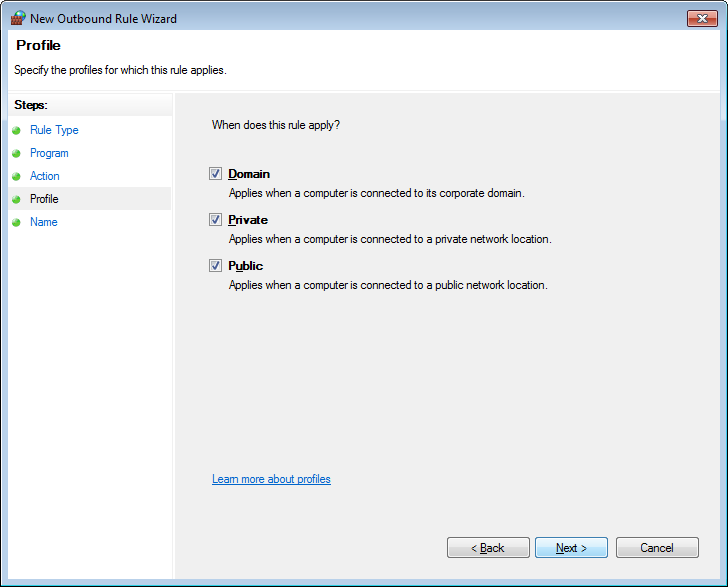
Keep them all checked, and click on the Next button. You will now be at a screen asking you to give this rule a name. Give it a descriptive name and then click on the Finish button. Once this rule is created, you need to use the same procedure again, but this time block the C:\Windows\SysWOW64\regsvr32.exe file.
Source:https://www.bleepingcomputer.com/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











