New study finds third-party updaters are riddled with critical vulnerabilities. The next time you’re in the market for a new Windows computer, consider this: if it comes from one of the top five manufacturers, it’s vulnerable to man-in-the-middle attacks that allow hackers to install malware.
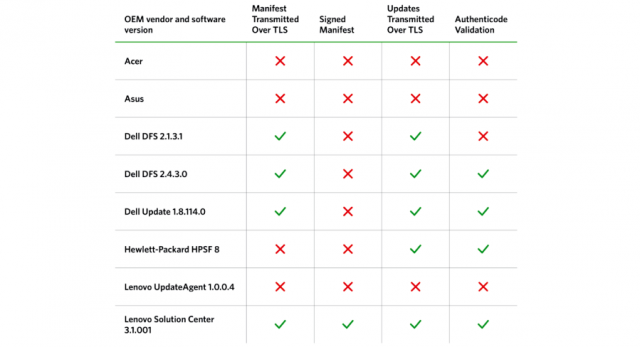
“Hacking in practice means taking the path of least resistance, and OEM software is often a weak link in the chain,” the Duo Security report stated. “All of the sexy exploit mitigations, desktop firewalls, and safe browsing enhancements can’t protect you when an OEM vendor cripples them with pre-installed software.”
In short, every single manufacturer was found to use pre-installed updaters that allowed someone with the ability to monitor a PC’s network traffic—say someone on the same unsecured Wi-Fi network or a rogue employee at an ISP or VPN provider—to execute code of their choice that runs with System-level privileges. The updaters are mostly used to deliver new versions of software and bloatware that come pre-installed on new PCs and are separate from Microsoft’s Windows Update, which is widely believed to be secure. The report provides a strong reason why it’s a good idea to wipe newly purchased machines and reinstall Windows minus all the custom crapware. At a minimum, third-party software should be uninstalled or blocked using a firewall.
Update: Lenovo has issued an advisory recommending customers uninstall the Lenovo Accelerator Application, which comes preinstalled on many notebooks and desktop systems running Windows 10. As the image at the top of this post illustrates, the Duo Security report uncovered several major shortcomings in the app’s update mechanism, including its failure to use any sort of encryption when checking for or downloading updates and the failure to validate digital signatures before installing them.
Source:https://arstechnica.com/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











