Tagged as “Ranscam”, Powershell and script-based malware is a botched smash-and-grab. There has been a lot of ingenuity poured into creating crypto-ransomware, the money-making malware that has become the scourge of hospitals, businesses, and home users over the past year. But none of that ingenuity applies to Ranscam, a new ransom malware reported by Cisco’s Talos Security Intelligence and Research Group.
Ranscam is a purely amateur attempt to cash in on the cryptoransomware trend that demands payment for “encrypted” files that were actually just plain deleted by a batch command. “Once it executes, it, it pops up a ransom message looking like any other ransomware,” Earl Carter, security research engineer at Cisco Talos, told Ars. “But then what happens is it forces a reboot, and it just deletes all the files. It doesn’t try to encrypt anything—it just deletes them all.”
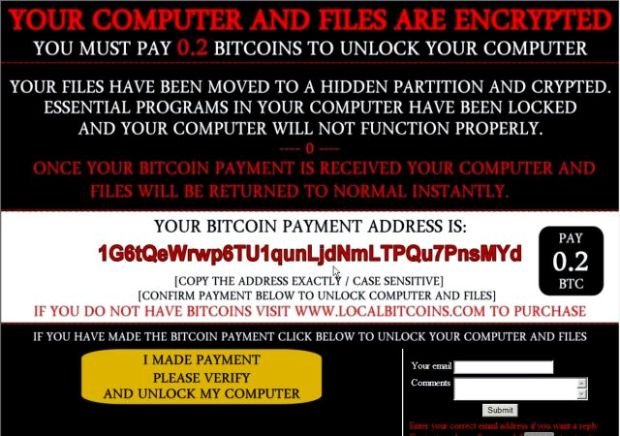
Talos discovered the file on the systems of a small number of customers. In every case, the malware presented exactly the same message, including the same Bitcoin wallet address. The victim is instructed:
“You must pay 0.2 Bitcoins to unlock your computer. Your files have been moved to a hidden partition and crypted. Essential programs in your computer have been locked and your computer will not function properly. Once your Bitcoin payment is received your computer and files will be returned to normal instantly.”
The message itself is an image file retrieved through an unprotected, unencrypted, unobfuscated HTTP request to a server hosted by Vitalix in Studio City, California, according to Internet address records. Clicking on the “button” after payment only results in the loading of another graphic, named “nopay.png,” which declares the victim’s payment has not been verified and one hostage file has been deleted as a result.
It goes on and on like this, but there’s really no point to it, as there is no hidden partition to begin with: all the files were deleted by a batch script launched by a Windows .NET executable—signed using a certificate registered to a domain [reca.net] owned by an Italian gas valve company—that uses PowerShell to simply delete files from specific directories. If stopped quickly enough, the files would likely be recoverable.
There have been only a handful of infections reported thus far, and the means of infection hasn’t been discovered. “Normally, these come in through phishing attacks,” Carter explained. “But this is not as widespread as some of the others, so it’s hard to say.” As for what the ransomware’s authors were hoping to achieve, Carter doesn’t think they thought very far ahead. “It’s confusing, because their whole model is a problem,” he explained. “If you don’t give people their files back, it’s unlikely they’ll pay.”
When researchers reached out to the scammers feigning ignorance through their e-mail address (a GMail account, cryptovirus32@gmail.com), the “ransomers” sent back an e-mail trying to explain how to buy and transfer BItcoin. They were helpful enough to explain as well that if they were doing cash transfers to buy Bitcoins on a Saturday, they should do it early before banks close. “Unfortunately we were unable to elicit further communication from the threat actor,” Edmund Brumaghin and Warren Mercer of Talos wrote in a blog post describing their research. “However, this highlights the continued willingness of ransomware operations to provide ongoing technical support to victims to maximize the likelihood that they will receive payouts.”
Carter said that the malware’s certificate was issued on July 6, 2016. A check of the activity for the Bitcoin wallet showed that it had seen no new transactions since June of 2016, so clearly this particular scam is fooling no one, or it’s largely being caught by network defenses before it lands.
Source:https://arstechnica.com/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.