There is a way to inject malicious content into email servers running email encryption appliances, a technique that allows attackers to go around email security products.
Email encryption appliances (EEAs) are hardware or virtualized devices that work together with email servers to encrypt and decrypt messages. EEAs are usually found in enterprise networks and are used to protect sensitive information exchanged via email, even if only one of the email correspondents is on a secure network.
Two security researchers from Securolytics — Vikas Singla & Jason Morris — discovered last week a flaw in how EEAs work, a flaw which allows an attacker to inject custom malicious emails inside EEAs. Once these emails inserted in the EEA, they flow inside a company’s internal email network infrastructure, reaching users’ inboxes.
Split Tunnel SMTP Exploit – the basics
This flaw, which they named the “Split Tunnel SMTP Exploit,” works as long as an attacker can discover the EEAs IP address, so the attacker knows where to inject his exploit code and malicious email. This isn’t as hard as it sounds.
Researchers said that any EEA accepting inbound SMTP connections is vulnerable to this attack, which works even if the EEA is a self-standing hardware device or a virtualized appliance installed on a company’s email server.
According to the Securolytics crew, an attacker can inject any payload type that supports MIME encoding. During their tests, they said they were able to inject emails with malicious content such as ransomware, macro-malware, phishing links, and password-protected archives (which in turn can hold a more varied attack arsenal).
Split Tunnel SMTP Exploit is meant to byass ESGs
An attack with the Split Tunnel SMTP Exploit is successful also because how email encryption appliances work with email servers and accompanying email security gateways (ESGs).
More accurately, the attack exploits network topology, and the path emails take through these appliances/servers before reaching a user’s inbox.
Securolytics experts say they found two methods of using this attack, which they tested on live email servers deployed at two healthcare clinics in the US.
Attack #1 – Going around the email security gateway
The first exploitation scenario relies on classic network setups where the email security gateway (ESG) and the email encryption appliance (EEA) are both behind a local firewall.
In these setups, both servers have a public IP address. The normal flow of an incoming email is through the ESG, which scans the email, and sends the email to the EEA (if necessary), which decrypts its content. From here, the EEA will forward the email message to the email server, which relays it to the correct user’s inbox.
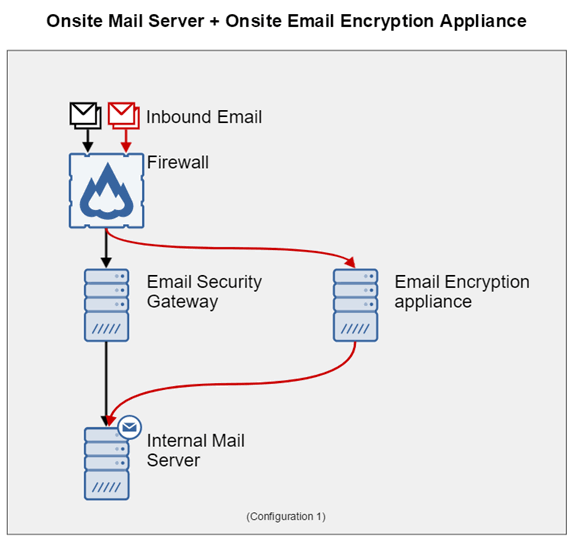
According to Securolytics experts, after an attacker discovers the EEA’s IP address, he can inject emails with malicious content right inside the EEA.
Because the EEA can’t tell if the email had come from the ESG and had been scanned, once it finishes decrypting the email’s content, the EEA follows normal procedures and forwards the email to the email server and the user’s inbox.
In this case, the Split Tunnel SMTP Exploit attack completely bypassed the email security product, allowing spammers and spear-phishers with a direct line to the user’s inbox.
Attack #2 – Messing up IP addresses
The second scenario where researchers were able to use the Split Tunnel SMTP Exploit attack was in network configurations where the email encryption appliance would sit in front of the email security gateway.
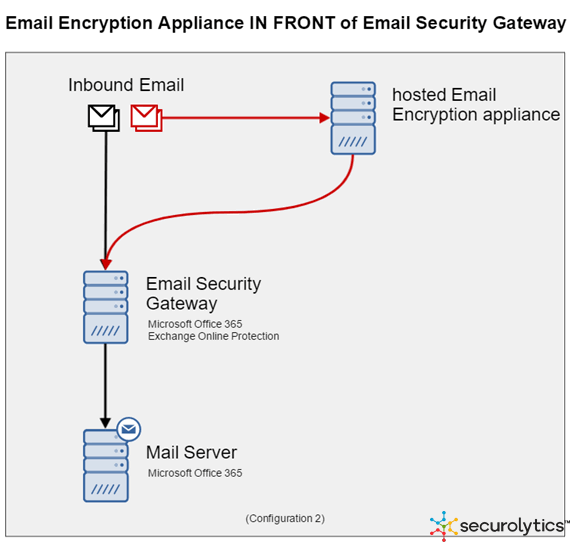
Even if network security experts devised this network topology to make sure dangerous content doesn’t slip by the ESG, Securolytics experts said the Split Tunnel SMTP Exploit attack managed to deliver malicious content to victims, despite going directly through the ESG’s scanner.
Again, an attacker would need to discover the EEA’s IP address and inject his malicious content inside the server. Emails created this way would have the IP address of the EEA appliance as the email’s origin, and not the attacker’s.
This would mask the attacker’s true origin, and forward malicious emails to the ESG coming from a whitelisted IP address.
No quick fix available
“We are unaware of any hotfix or patch that will fully protect against this exploit,” says the Securolytics team. “Organizations will need to invest time and resources to identify and implement the best solution.”
For their part, the two experts recommend that companies:
Completely disable transparent gateway-to-gateway encryption on the encryption appliance.
Implement a parallel processing solution that can perform email decryption and threat detection at the same time.
Source:https://www.bleepingcomputer.com/news/security/split-tunnel-smtp-exploit-allows-an-attacker-to-inject-payloads-into-email-servers/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.