Yesterday, Malwarebytes malware researcher Marcelo Rivero discovered a new variant of the CryptoMix ransomware that is appending the .EXTE extension to encrypted file names. This article provides a brief summary of information related to this new variant.
As we are always looking for weaknesses, if you are a victim of this variant and decide to pay the ransom, please send us the decryptor so we can take a look at it. You can also discuss or receive support for Cryptomix ransomware infections in our dedicated Cryptomix Help & Support Topic.
Changes in the Exte Cryptomix Ransomware Variant
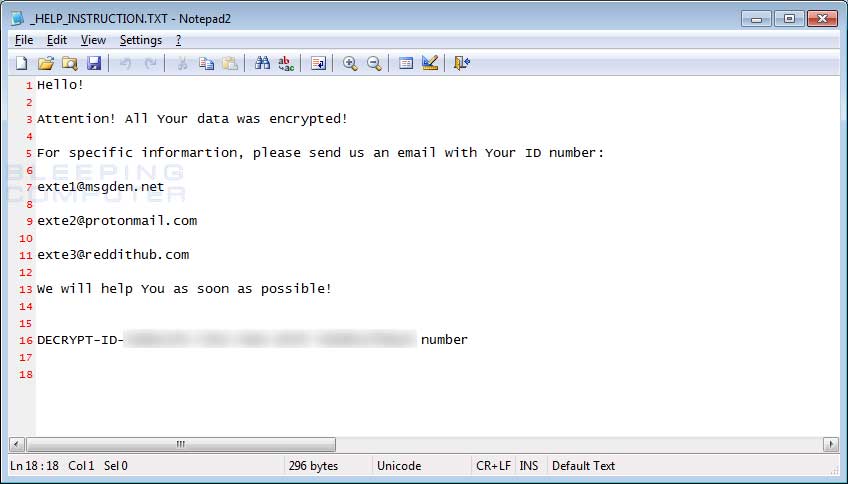
While overall the encryption methods stay the same in this variant, there have been some differences. First and foremost, we have a new ransom note with a file name of _HELP_INSTRUCTION.TXT. This ransom note contains instructions to contact either exte1@msgden.net, exte2@protonmail.com, or exte3@reddithub.com for payment information.
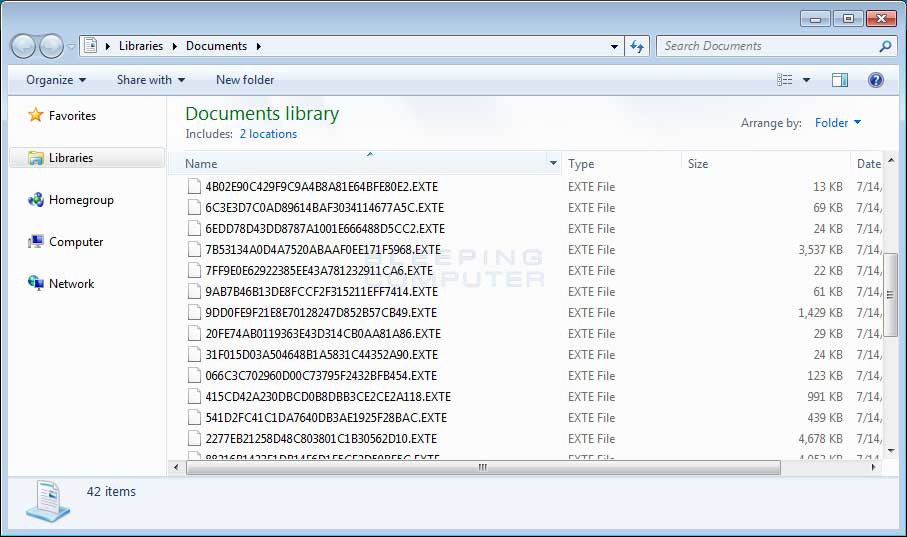
The next noticeable change is the extension appended to encrypted files. With this version, when a file is encrypted by the ransomware, it will modify the filename and then append the .EXTE extension to encrypted file’s name. For example, an test file encrypted by this variant has an encrypted file name of 32A1CD301F2322B032AA8C8625EC0768.EXTE.
One point of interest, is that this variant continues to use the same 10 public RSA keys as the previous AZER version. One of these keys will be selected to encrypt the AES key used to encrypt a victim’s files. This allows the ransomware to work completely offline with no network communication.
As this is just a cursory analysis of this new variant, if anything else is discovered, we will be sure to update this article.
IOCs
File Hashes:
SHA256: 6211fdd680208f94aa0149619facc0de8b51e6cb98108132d539469f3affa712
Filenames associated with the Exte Cryptomix Variant:
_HELP_INSTRUCTION.TXT
%AppData%\[random].exeExte Ransom Note Text:
Hello!
Attention! All Your data was encrypted!
For specific informartion, please send us an email with Your ID number:
exte1@msgden.net
exte2@protonmail.com
exte3@reddithub.com
We will help You as soon as possible!
DECRYPT-ID-[victim_id] number
Emails Associated with the Exte Ransomware:
exte1@msgden.net
exte2@protonmail.com
exte3@reddithub.comBundled Public RSA-1024 Keys:
-----BEGIN PUBLIC KEY-----
MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQCfBni3t7uANs2aVmoh33h/gUlA UMlLAIYgjIQx0cdategi5Gs6SubFxGLoJgjR1TkYXnhB9UxlKCqsAaKSAegQMLRM 7HN/h6eZN7PaLMfFf/aJgZJe0FuaV/CABEvGopt5VqR3GJLzhgl/qttgsCTQcPFC G4gRBgdJ0Uqdq6Pe1wIDAQAB
-----END PUBLIC KEY-----
-----BEGIN PUBLIC KEY-----
MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQCTp02+iahQUVQQSGTYcAgUdyn8 R6D3+q/M1GwA4c6ePwXlsEJC8UC4hDE4otjs4Vae0MauQrvkYo2rnilCpiqsv0Oo OjDgOHhHI1vUILpWjAVRu61DORWqdvQEH3x9GfGRIulKwhVdzll5sGS9pyGWAAGq XvJ8T/ods5V+M3nFvQIDAQAB
-----END PUBLIC KEY-----
-----BEGIN PUBLIC KEY-----
MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQC2Zs4/PG+bhEhduEnmB/zS4Ps7 bD0EDn6q2tgpIwu7WF4NhDwnCQYeX9uweOs+x3pPKIHgZj7KtyOdwjJEMYt4yago kMnp24CM413CbGz28tsSLifJpcDq7NdFlItv1foqE3EhxK4RnnsKRnlNnZOmJobj BXWAK7kI6PMjAsycjQIDAQAB
-----END PUBLIC KEY-----
-----BEGIN PUBLIC KEY-----
MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQDdcVWIUztGfqsyayX8MJ+MilwA OCMmaedwUkhcrOaZbEr/kjFAS/51dhxfUmoO2M6N51D1+Tlx1hFP0Bbea41ory14 /jXmBP/ARTPejT9wmAcdFSYL5RKqn21imymnSfllV7lLSS7fwzIhUibz/c13pk1w UFQpsQKlAmge6nPWMQIDAQAB
-----END PUBLIC KEY-----
-----BEGIN PUBLIC KEY-----
MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQCoXHPF5pGepB37MwkGshTi4N+q KaRbRAk6b6tDUxHK8AWyNDJTFKLygvaNTxjAcpY467SDTXQq6EyvaCh2juaSzCLH qxcwIVRMH4mtBI8RKx5bycWssbuZD6XwQpcS7WABqE8+BuYDmALgeh1W0UVBQge5 Alv8dKw5oY2B84RApQIDAQAB
-----END PUBLIC KEY-----
-----BEGIN PUBLIC KEY-----
MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQCfshy8WocDLQBfn36LclXu7obD X5hCJFAKntVU3Siyy6XKnumyu/qsiwekxG0QkDrEuWZWGk+/w5qVf+bw1wXbKnBr h2FiYqtXgN8pX7h6vDhYNWd80RKg0fxA7sRYoB7HCtel99BCcGOKvWbsr9hcFq3j EPtf81OdtqlTI6x6uwIDAQAB
-----END PUBLIC KEY-----
-----BEGIN PUBLIC KEY-----
MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQC3ncKb3ppnuXs7NtizXtdHcKcj sfSIhS3E23j5Z4pxYfj3c3ipP8/gxu93/9b6qSQnQ87NRACf8NBbpr1XYR1kGkNK cRk+u1QsKsVyYP8QoMtnCPbxaIAxZ9qc2o8eFPt44IbOFNo4TS682ZnrgvCIl/D+ taf9I8jbrBTSbfxQ3wIDAQAB
-----END PUBLIC KEY-----
-----BEGIN PUBLIC KEY-----
MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQCNdG6Kp5B6EHKVsENf2QudkLfe TMzETNDGBk5cvGpj3On70vZGODVj/WfRe2iHyVE0ykT/iXXtb/C5gw3FePCSGVja 5S3qH9xh6Ncw5sFrsdgBbm7qPYSbRmux2VTjHlLE44ckkTTCSiTUL3KX/08cU04V hb/JtNwKF5bg3ycuhQIDAQAB
-----END PUBLIC KEY-----
-----BEGIN PUBLIC KEY-----
MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQCqqapIMkQJgyt8mfVLZRPIEU20 V8c3+JbWNCdtDrIucv5nsKxJ/hCCDCau8gVjNN5jWtLltoQ0NvwR94HZaUkXAjGq Iy+vvpc66SBLin8pJ/DzLtA3ouQBrYU2/9C75DrKGuCedEoAzoFkCjz/AokqjTkz xSIkf+5//Rpoj22lHwIDAQAB
-----END PUBLIC KEY-----
-----BEGIN PUBLIC KEY-----
MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQCHZ0EKaGTzyOxqaX2ePqAs46RU HhLRsApVWfO0z3BADXv4cv2iGjSXRZE1g7dU/KNEVZrjuBRaHksWpXKIwI6v7vSJ ZcxsaNRZNS+RTwJbu5VNc5uHBc5YPa7sdqocVrt3b6eXXPbn5gZcQY3L18TTd+S3 DljCC6h8BC80BJI6OQIDAQAB
-----END PUBLIC KEY-----
-----BEGIN PUBLIC KEY-----
MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQCkrR8CoTgor4sIybnVarCSWzMN RIoH51qIgCWDx49UQYXXqCn7I4T2XL7iOD5Fb/LO8LLS/BC7xNETIBGwUsOLMUXq 0LT3wlASZX4l491JPAAzlGfspmWqOnxwFZh4e2kqbix9uTGRw7oC0v7n6pACJSLW ybODvrXAfJlITYUYIQIDAQAB
-----END PUBLIC KEY-----
https://www.bleepingcomputer.com/news/security/new-exte-cryptomix-ransomware-variant-released/Source:

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











