Microsoft has developed multiple protection mechanisms against some popular hacking variants, including the malicious use of macros. Sometimes, threat actors send Office files in which affected users must enable macros to complete the attack, triggering malware download, information theft, and even remote access.
Despite protection mechanisms (such as the bar indicating the disabling of macros), malicious hackers continue to resort to abusing macros for their attack campaigns, so Microsoft has had to devise new security methods. The most recent of these mechanisms is a default change for five Office applications that run macros.
Microsoft announced that, for macros in files on the Internet, users will no longer be able to enable macros with just one click; instead, a button with more information about the file and macros will appear, so the company hopes that users will have more information at hand about potential security risks.
On the other hand, when you download an untrusted Office file with macros included, a “Learn More” button will appear to inform the user that the file contains Visual Basics for Applications (VBA) macros.
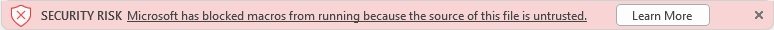
By clicking on “Learn More”, users will be redirected to an article with information about phishing techniques, malware deployment and other hacking variants related to the use of macros. Removing Mark of the Web (MOTW) can also prove useful against macro attacks. This is an attribute that Windows adds to files when it is obtained from an untrusted location.
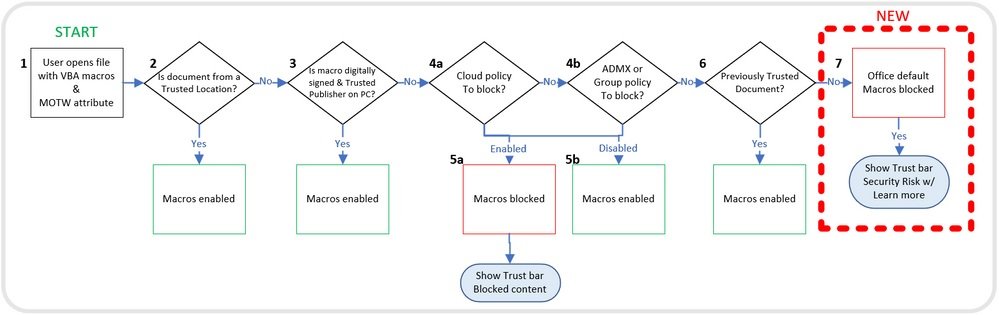
System administrators can use the “Block macros from running on Office files from the Internet” policy to prevent users from inadvertently opening Internet files that contain macros. Microsoft recommends that you enable this policy to avoid problems related to these default changes.
Finally, Microsoft issued a couple of additional recommendations:
- Open files from a trusted location
- Open files with digitally signed macros and provide the certificate to the user
A full report on the new configurations against macro attacks is available on the company’s official platforms.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











