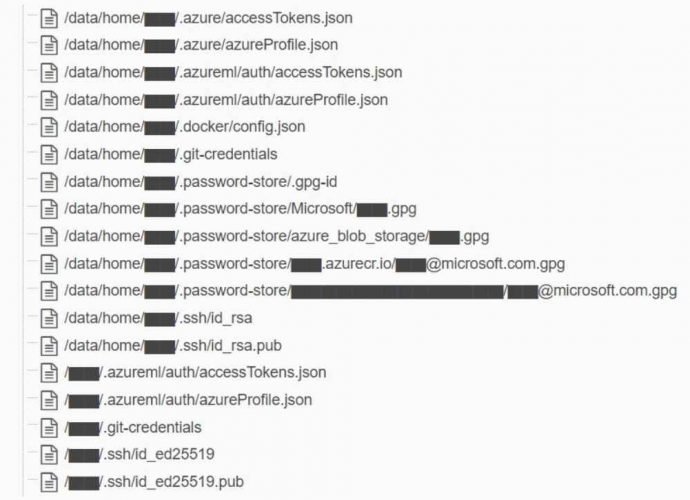
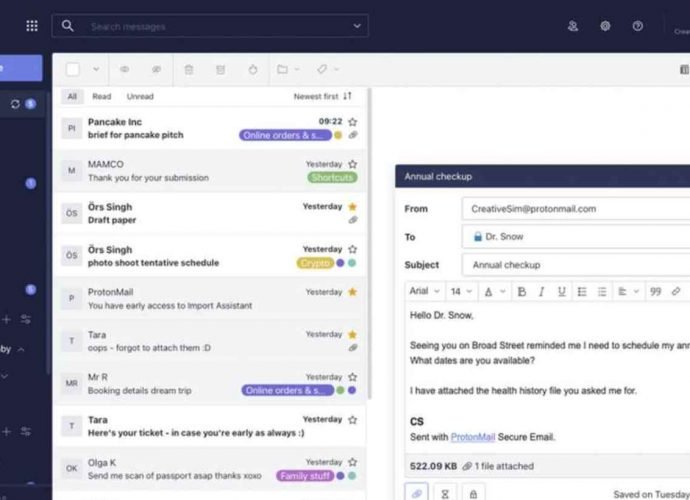
How this Israeli Backdoor written in C#/.NET can be used to hack into any company
As part of an ongoing cyber espionage effort, the Iranian nation-state hacking group known as OilRig has continued to target government entities in the Middle East. This cyber espionage campaignRead More →