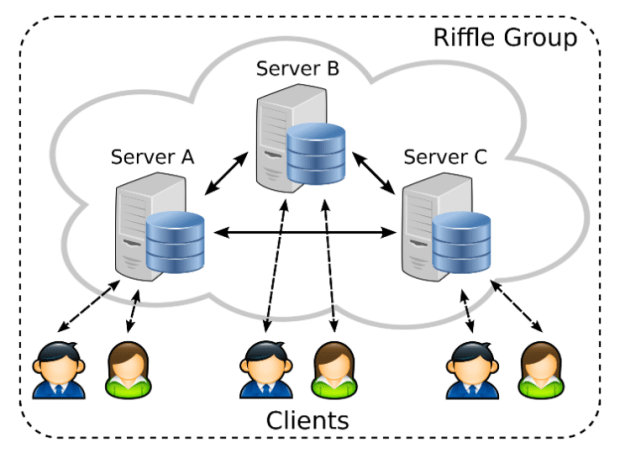
MIT’s anonymous online communications protocol Riffle could beat Tor at its own game
Tor has been the go-to for anonymous communication online for years now — and that has made it one of the juiciest targets possible to the likes of the NSARead More →