The First Person to Hack the iPhone Built a Self-Driving Car. In His Garage
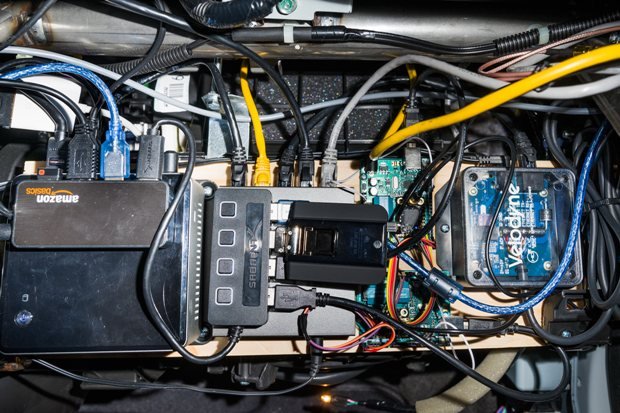
A few days before Thanksgiving, George Hotz, a 26-year-old hacker, invites me to his house in San Francisco to check out a project he’s been working on. He says it’sRead More →